Introduction
In this post, I will demonstrate how an email can be sent using Telnet — often mimicking spam or spoofed emails — and how to analyze the message headers to trace its source. I’ll also show you how to delete all emails from all mailboxes using a PowerShell script (for example, in an Exchange environment).
1. Sending Email via Telnet (Spoofed Example)
Telnet can be used to simulate an SMTP conversation manually. This is useful for testing or understanding how SMTP works, but also highlights how easily spoofing can occur if proper protections aren’t in place.
Steps:
telnet mail.example.com 25
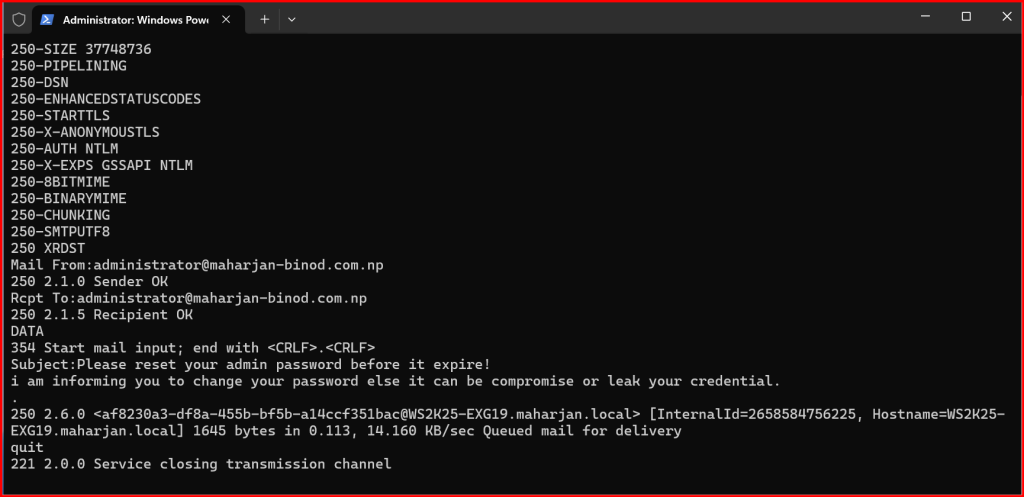
SMTP Conversation:
HELO attacker.com
MAIL FROM:spoof@trusted.com
RCPT TO:victim@example.com
DATA
Subject: Test Spoofed Email
From: Trusted User spoof@trusted.com
To: Victim victim@example.com
This is a spoofed test message.
.
QUIT
🛡️ Note: This only works if the receiving server does not have anti-spoofing protections such as SPF, DKIM, or DMARC properly enforced, and if the Receive connector is not configured correctly.
1.1 What if? User Mailbox password compromised and send email using VPN/Proxy
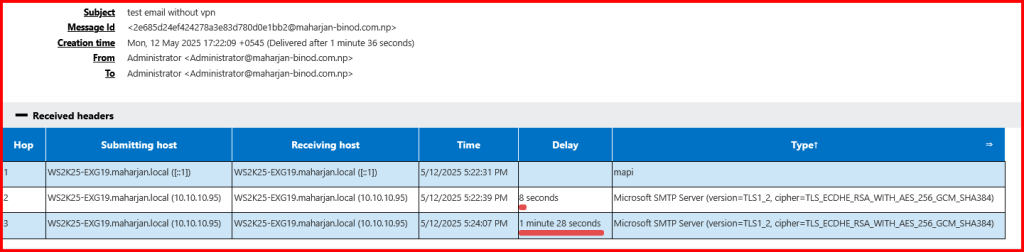
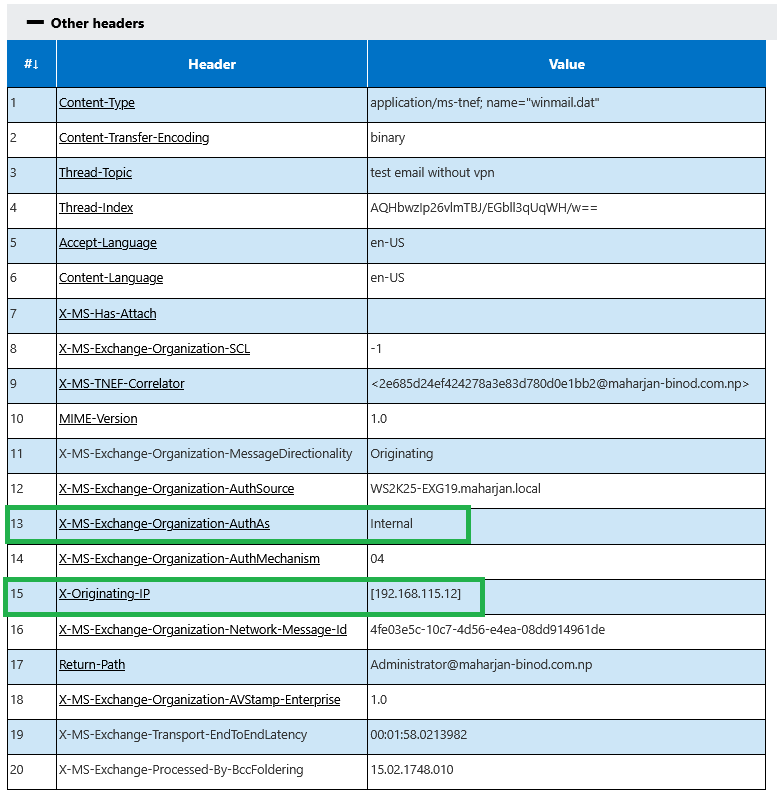
Analyze Message header and Check for Originating IP address Nature either Private IP or Public IP (Can be VPN used IP if used)
2. Analyze Message Header
Once the spoofed message arrives, examine the headers from Outlook or any email client:
- Return-Path — Who actually sent it.
- Received — Each hop the message took.
- Authentication-Results — Whether SPF, DKIM, DMARC passed or failed.
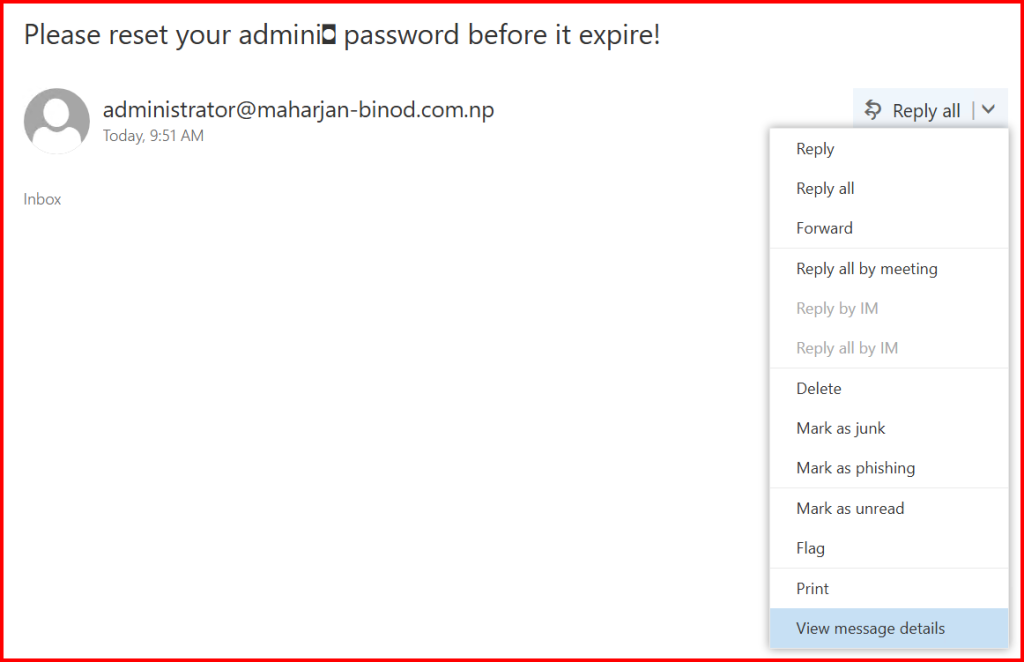
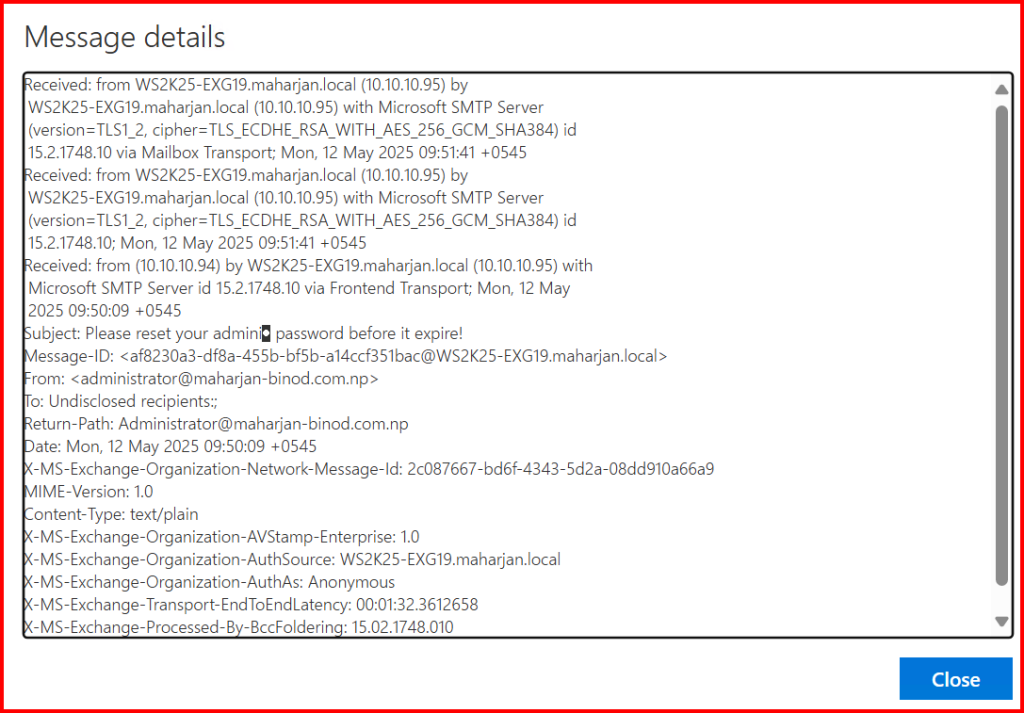
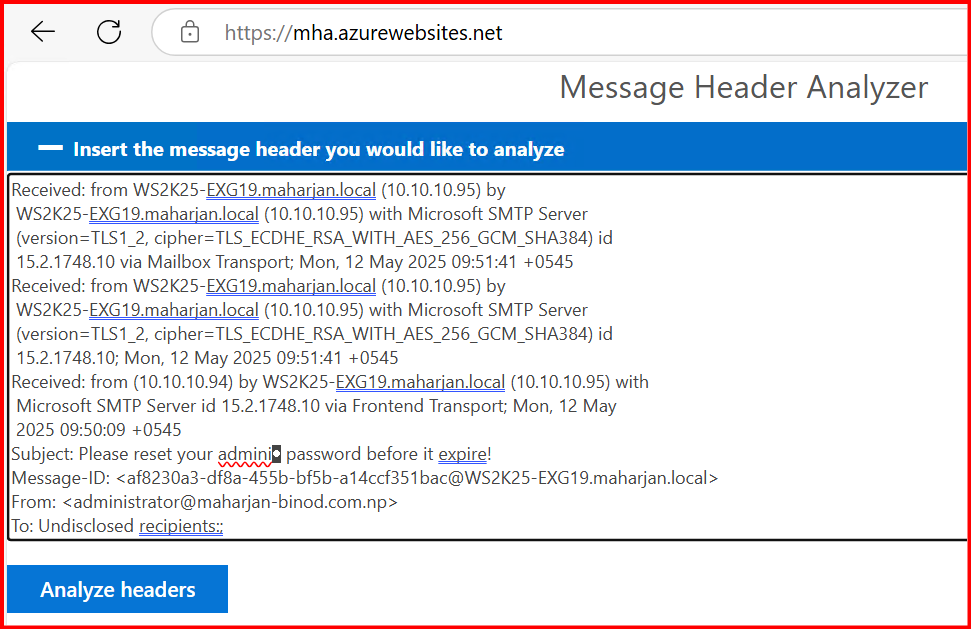
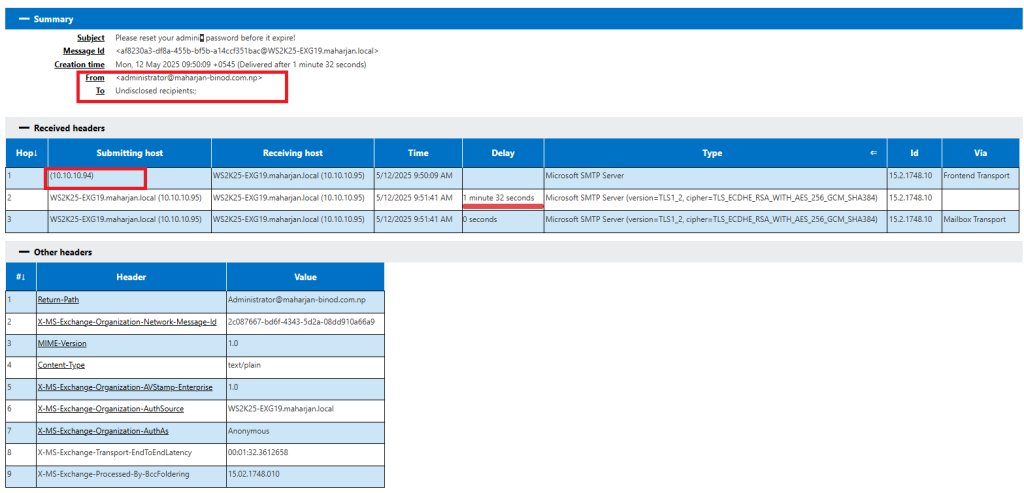
This message was likely spoofed and injected into your Exchange environment bypassing proper authentication and anti-spoofing checks. Here’s why:
- No SPF, DKIM, or DMARC checks occurred.
- Sent anonymously from a private IP.
- No clear recipient (“To”) header.
- The From address is spoofed.
3. Delete All Emails from All Mailboxes via Script (Exchange)
⚠️ Warning: Use with extreme caution. This is a destructive operation.
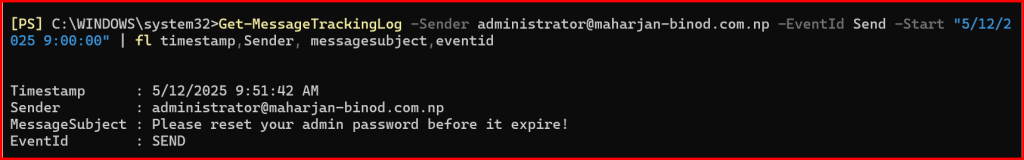
Get-MessageTrackingLog -Sender administrator@maharjan-binod.com.np -EventId Send -Start “5/12/2025 9:00:00” | fl timestamp,Sender, messagesubject,eventid
New-ManagementRoleAssignment –Role "Mailbox Import Export" –User "administrator"
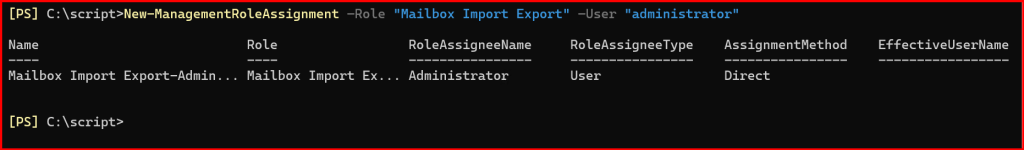
Note: Re-open Exchange Management Shell (EMS) and below command.
3.1. Delete email from single mailbox via PowerShell script:
Download script and save it as .ps1 extension for Single mailbox:
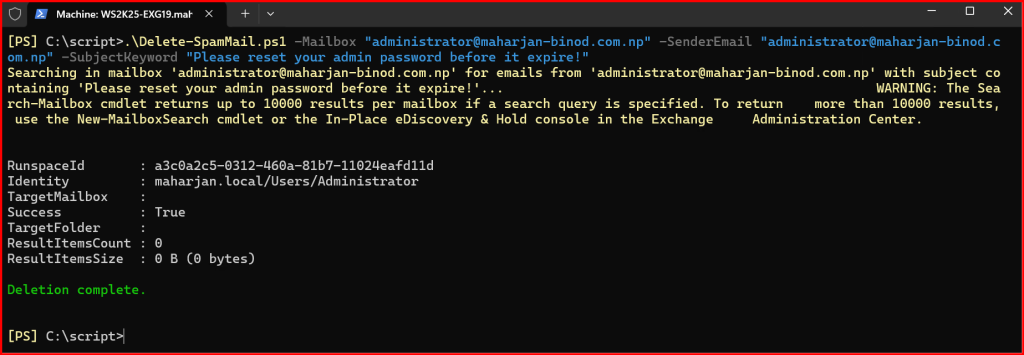
.\Delete-SpamMail.ps1 -Mailbox “
administrator@maharjan-binod.com.np” -SenderEmail “
administrator@maharjan-binod.com.np” -SubjectKeyword “Please reset your admin password before it expire!”
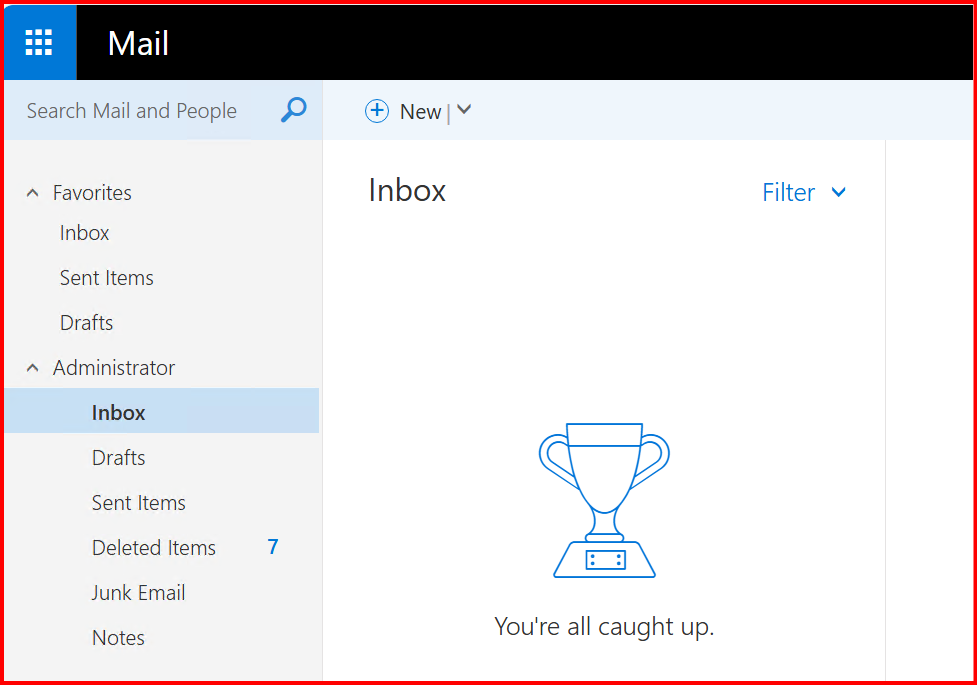
Email Deleted from Inbox:
3.2. Delete email from all mailboxes via PowerShell script:
Download script and save it as .ps1 extension for bulk mailboxes:
.\Delete-SpamMail.ps1 -SenderEmail ” administrator@maharjan-binod.com.np” -SubjectKeyword “Please reset your admin password before it expire!”
Conclusion
This post demonstrates:
- How easily spoofed emails can be sent using Telnet.
- How to investigate headers to trace the origin.
- And how to perform email cleanup using PowerShell.
Always ensure anti-spoofing controls (SPF, DKIM, DMARC) are properly configured and enforced on your mail servers to reduce such risks.

Leave a Reply