Introduction
In this post, I will walk you through how I configured and tested Multi-Factor Authentication (MFA) using ManageEngine ADSelfService Plus for both Windows endpoints and Exchange OWA. I set this up in my lab environment, which includes:
- An Active Directory (AD) server
- An Exchange 2019 server
- A ManageEngine ADSelfService Plus server
- A client machine (Windows 10/11)
This guide will help you secure access to both OWA and Windows login with MFA.
🔧 Step 1: Setup Lab Environment
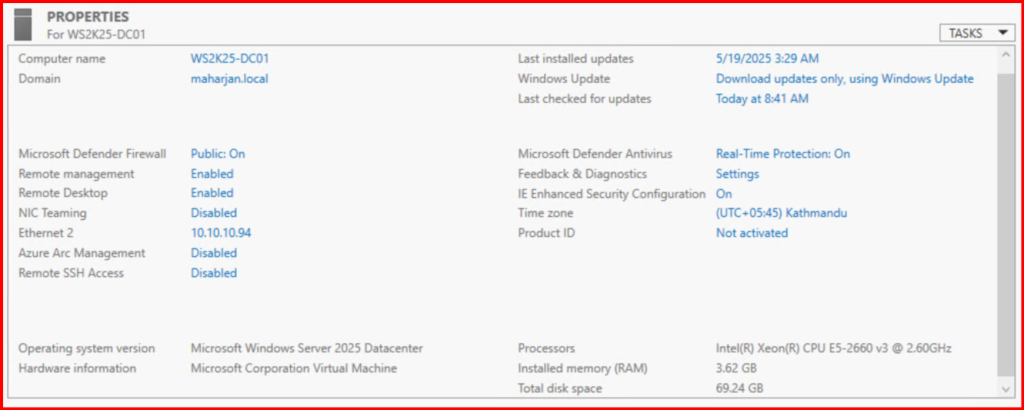
1. Install and configure Active Directory
- Ensure AD is functional (ADDS,CA & DNS).
- User accounts are created for testing.
Refer this link for AD Domain Server setup: ACTIVE DIRECTORY DOMAIN SERVICES
Refer this link for AD CA Server setup: ACTIVE DIRECTORY CERTIFICATE SERVICES
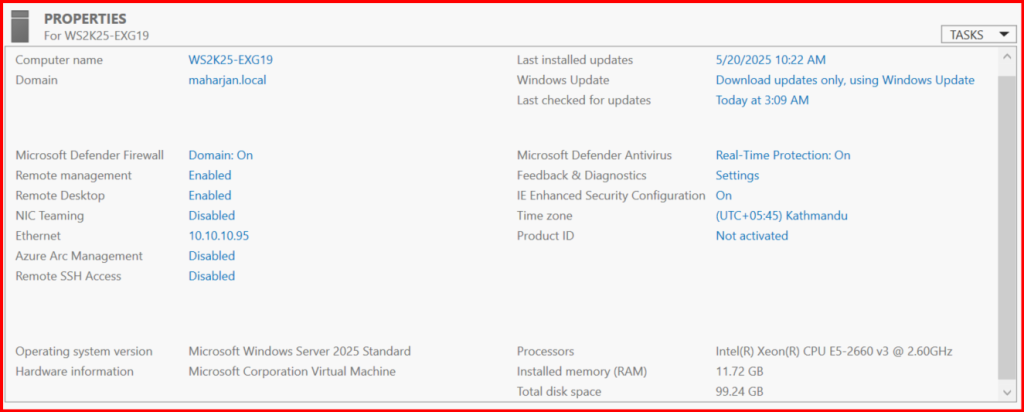
2. Install Exchange Server (2019)
- Ensure OWA and ECP are accessible.
Refer this link for Exchange Server setup: Installing Exchange Server 2019 on Windows Server 2025
3. Install ManageEngine ADSelfService Plus
- Download the latest version from the ManageEngine website.
- Install on a dedicated Windows Server VM.
- Ensure the server is joined to the domain.
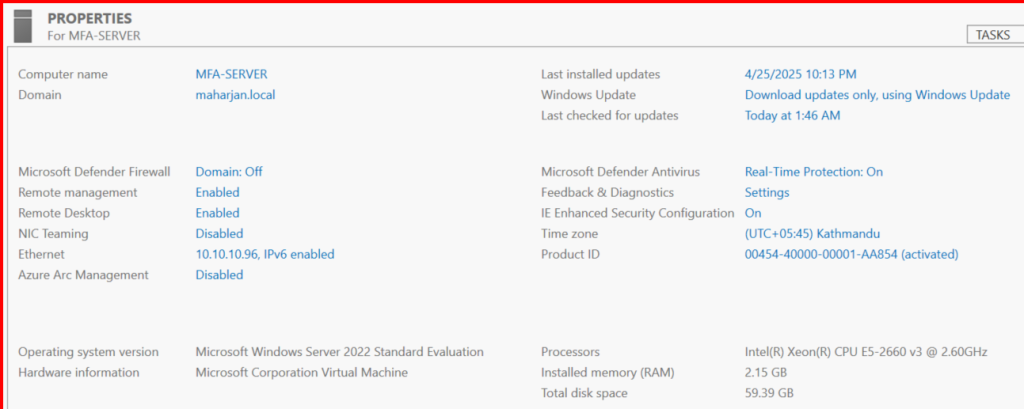
Refer this link to setup ADSelfService Plus: Installing ADSelfService Plus
🔐 Step 2: Integrate ADSelfService Plus with Active Directory
- Launch ADSelfService Plus web portal.
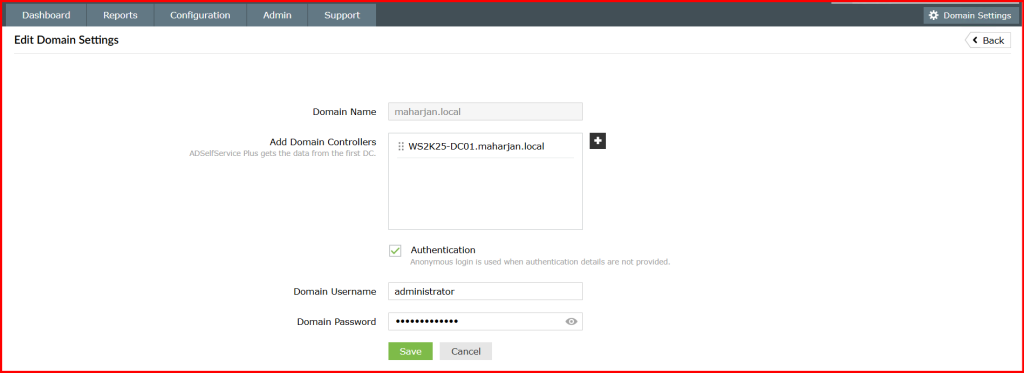
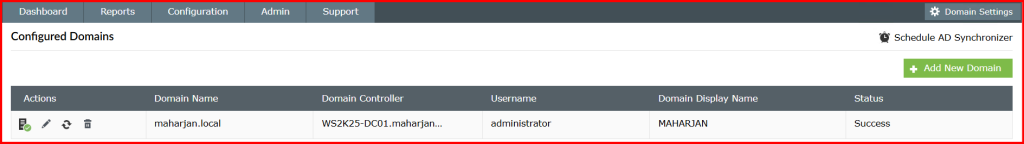
- Go to Admin → Configuration → Domain Settings.
- Add your AD domain and enter a privileged domain account.
- Test the connection to confirm it’s successful.

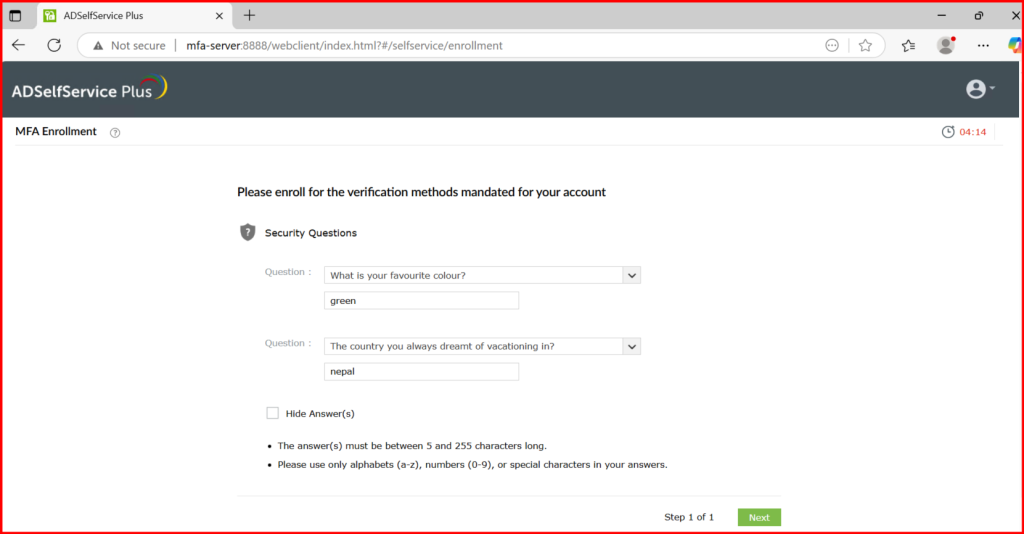
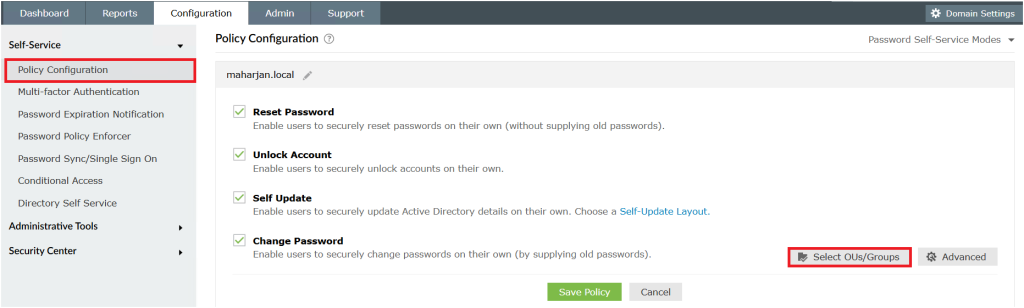
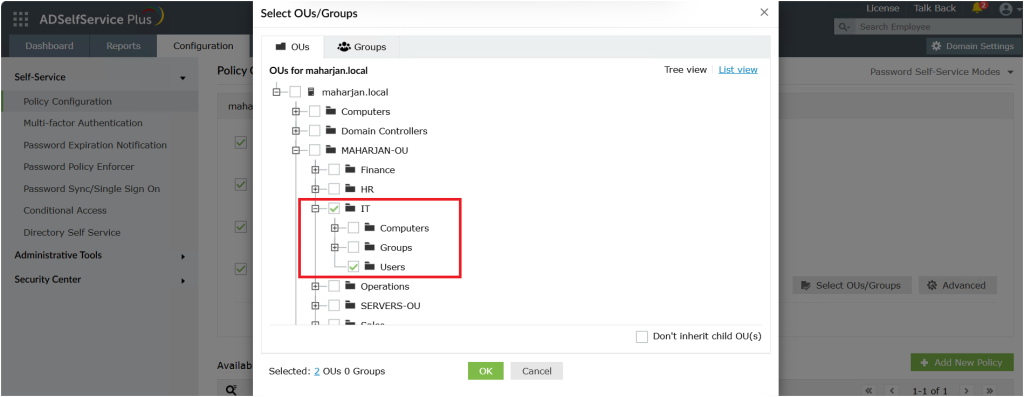
5. Go to Configuration → Under Self-Service >Policy Configuration → Select OUs/Groups
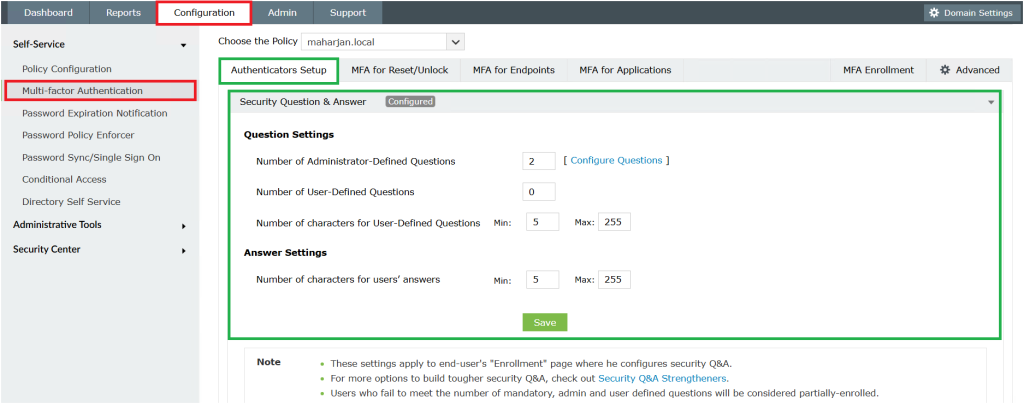
🛡 Step 3: Enable MFA for Windows Logon (Endpoints)
Go to Configuration → Under Self-service> Multi-factor Authentication → Authenticators Setup.
- Choose the authentication methods (e.g., Microsoft Authenticator).
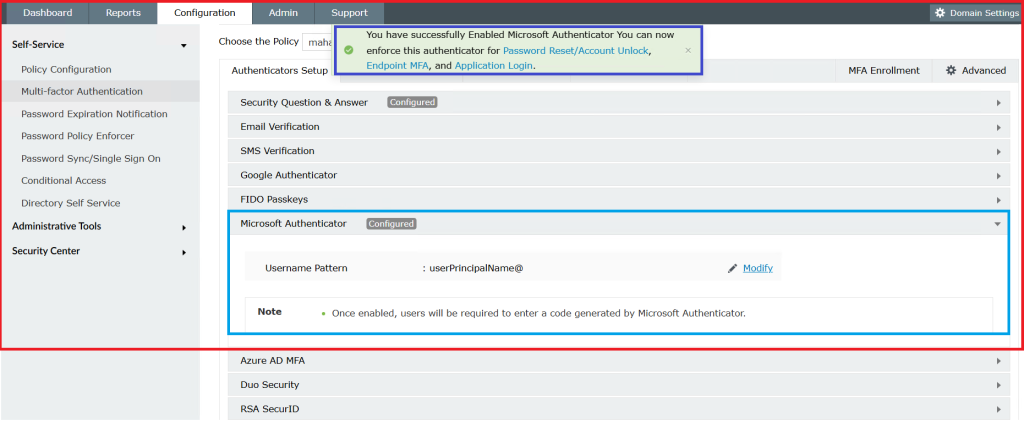
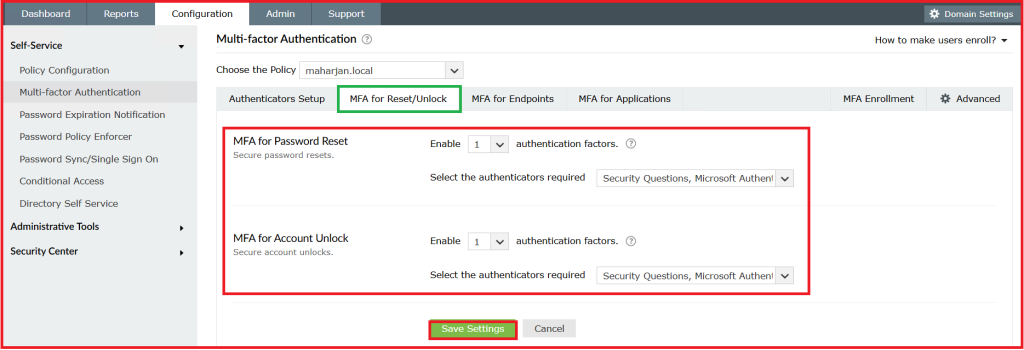
2. Configure settings for MFA for Reset/Unlock.
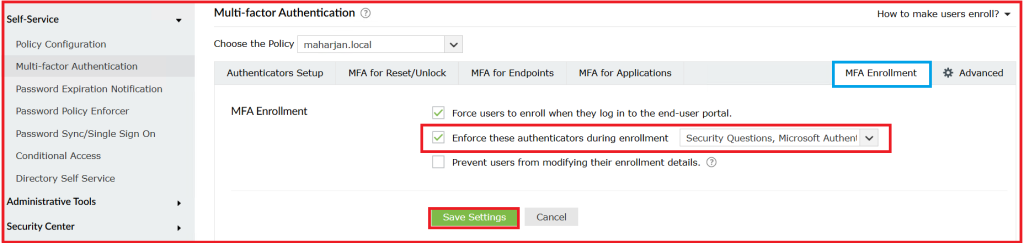
3. Configure MFA Enrollment Setting.
4. Configure MFA for Endpoints.
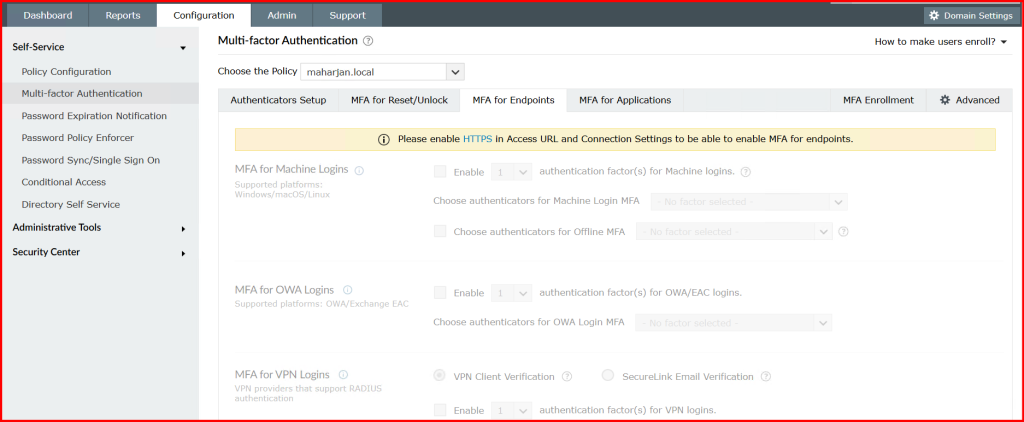
4.1. Enable HTTPS service for MFA Endpoints (Mandatory):
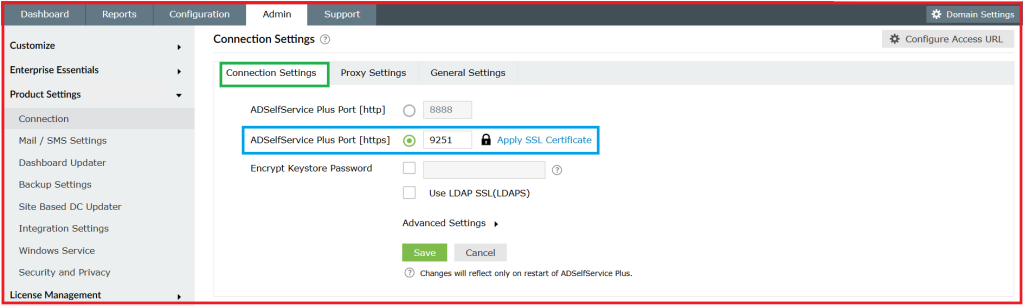
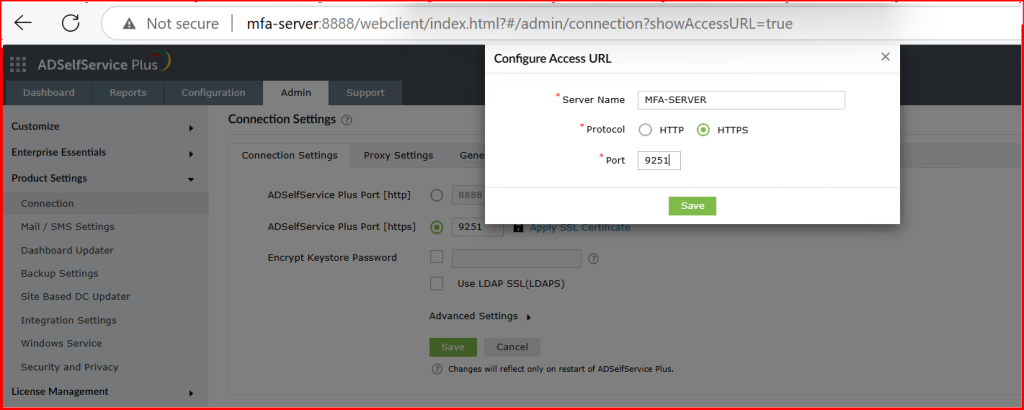
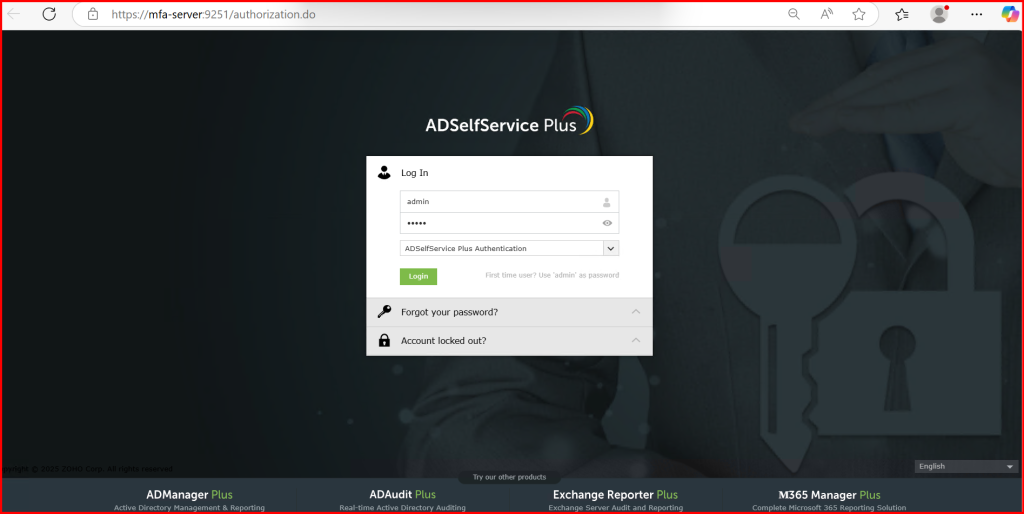
Refer to link for Internal CA Self-Signed certificate: 🛡️ How I Secured ADSelfService Plus Web Server with an Internal CA Certificate
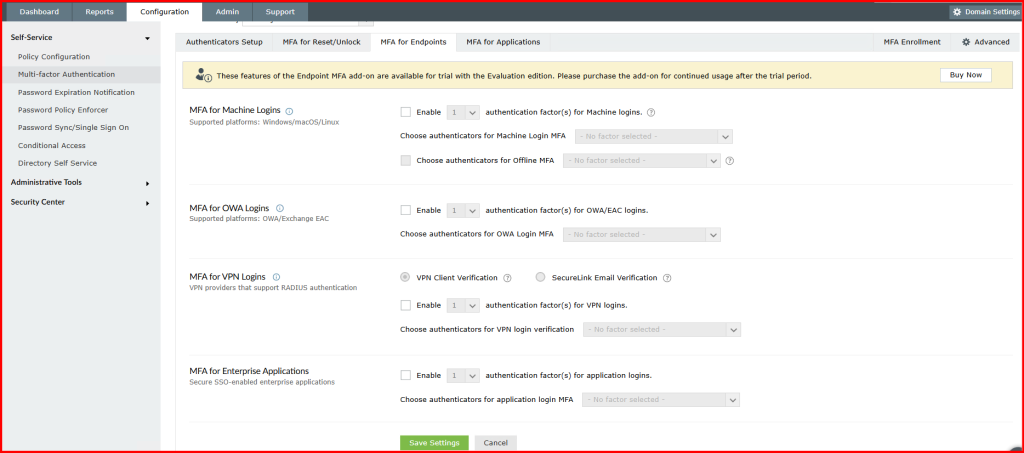
4.2. Enable MFA for Machine Logins (Endpoints)
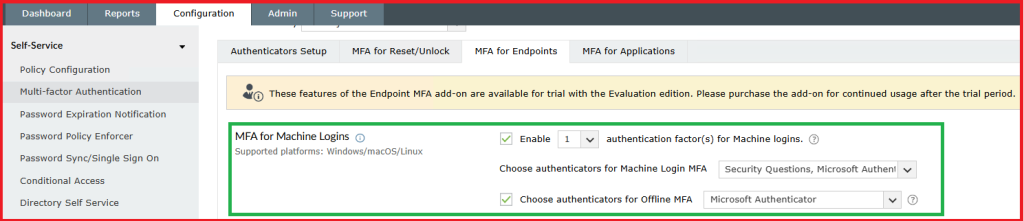
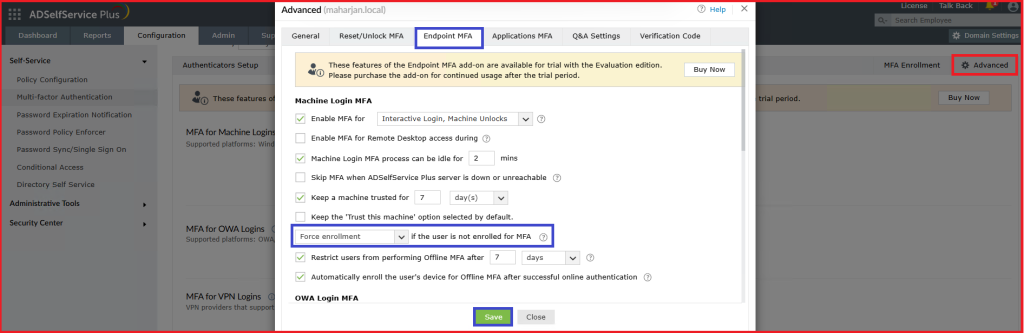
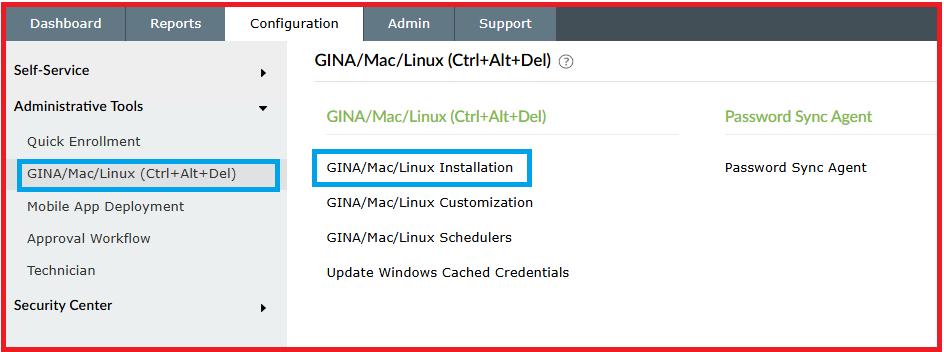
4.3. Install Agent on the client machine:
- Navigate to Configuration → Under Administrative tools> GINA → GINA Installation.
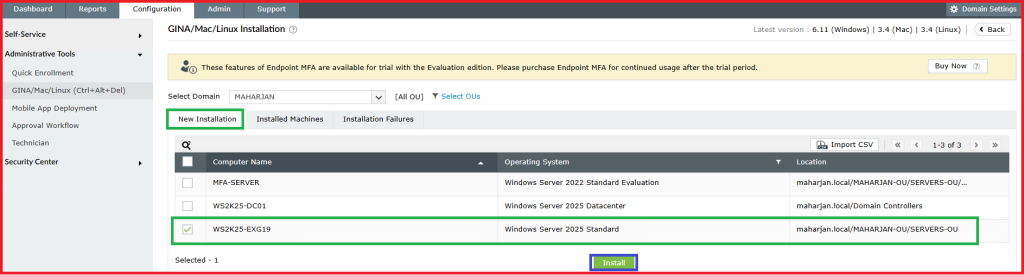
2. Select the Server for installation.

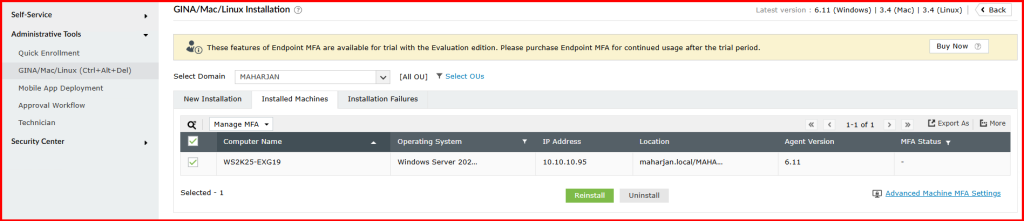
4.4. Verify installation on the client machine:
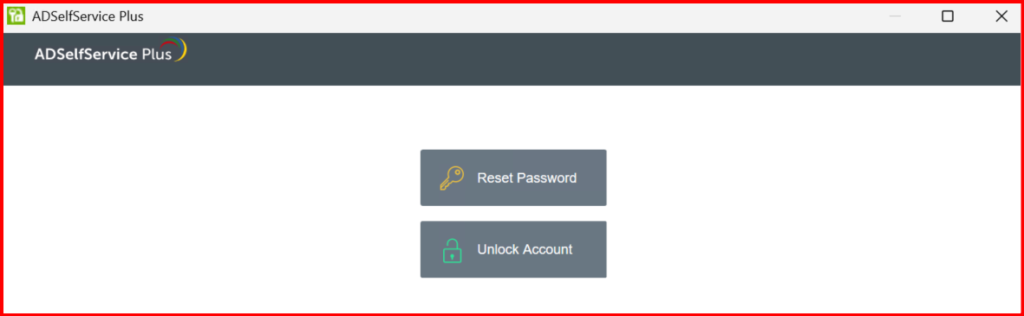
🌐 Step 4: Enable MFA for Exchange OWA
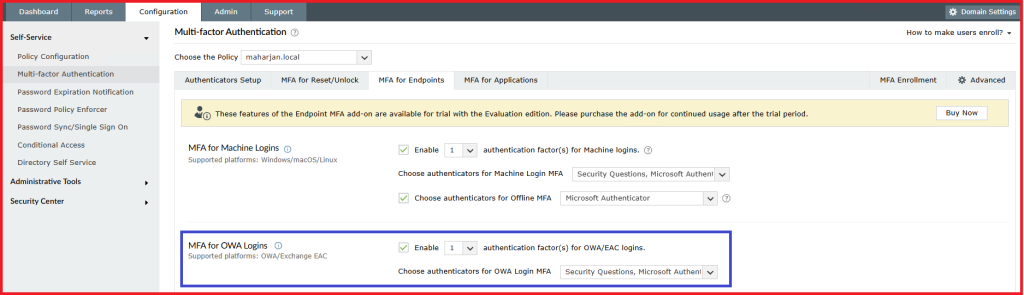
- Go to Configuration → Under Self-service> Multi-factor Authentication → MFA for Endpoints
- Select Exchange OWA and ECP.
- Enable MFA and select the authentication factors.
4. Install and configure the OWA Connector on the Exchange Server:
- Download from ADSelfService Plus under Integration.
- Install and follow prompts to register with ADSelfService Plus.
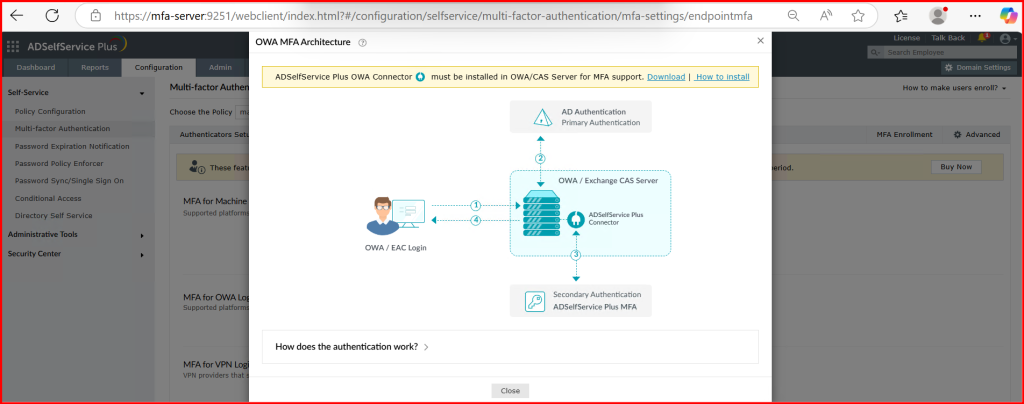
Refer this link for installing OWA Connector in Exchange server: MFA for OWA Login
Downloaded the Module from Site in Exchange server 2019:
Install Module in PowerShell:
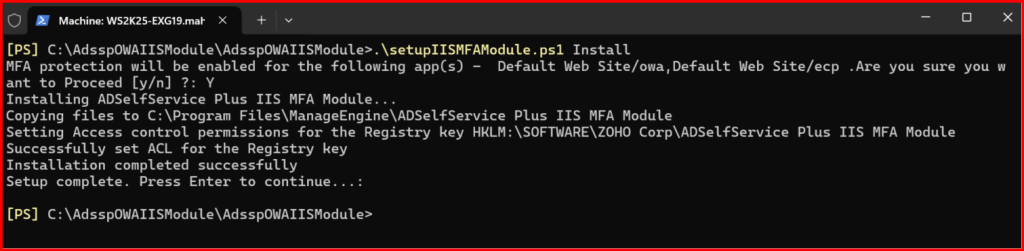
Note: If need to uninstall: .\setupIISMFAModule.ps1 UnInstall and delete the folders.
5. Restart IIS on Exchange Server: iisreset
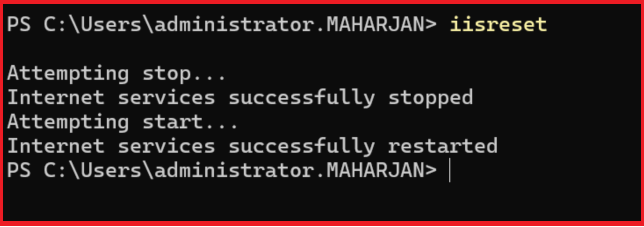
🧪 Step 5: Test MFA Functionality
- Test Windows Endpoint MFA:
- Log out from the client machine.
- Log back in with test user credentials.
- Verify MFA challenge appears.
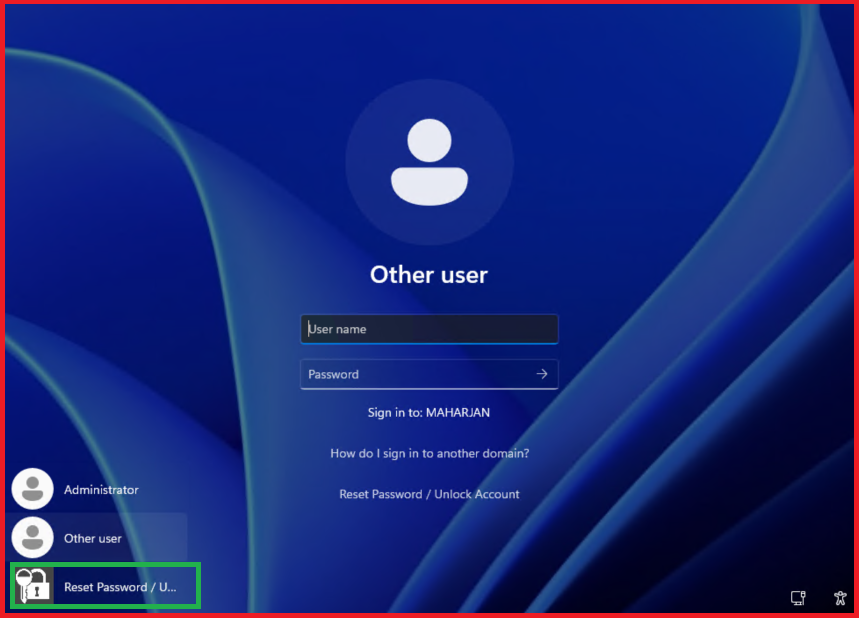
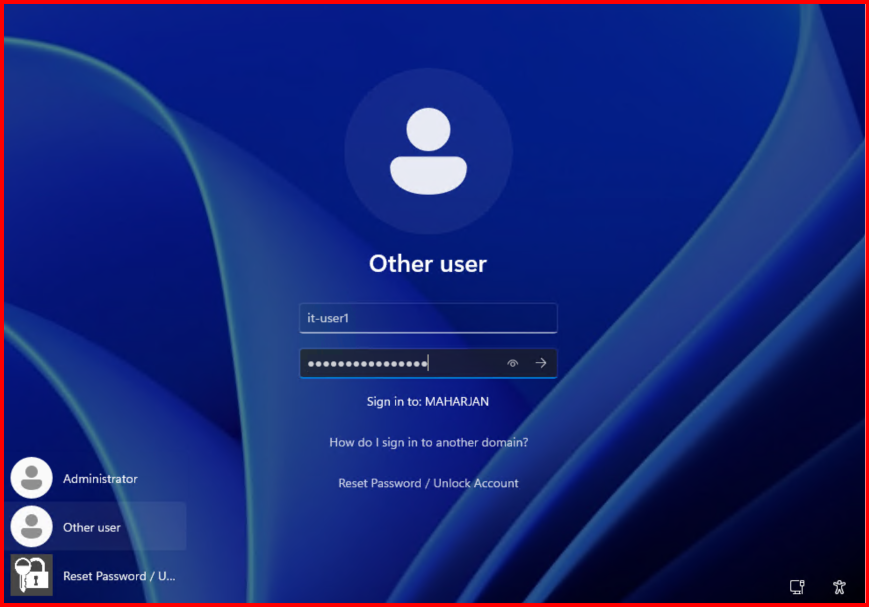
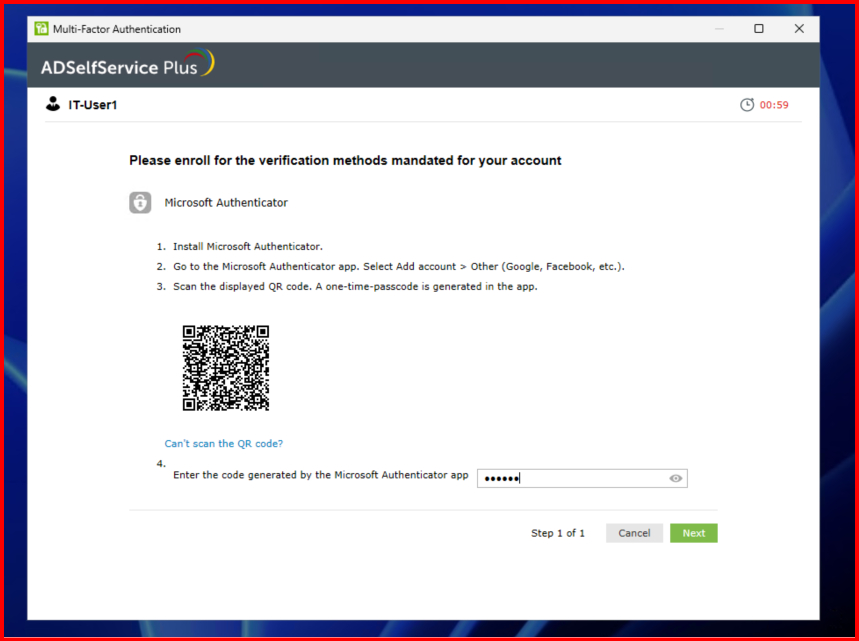

Already MFA configured: Re-login.
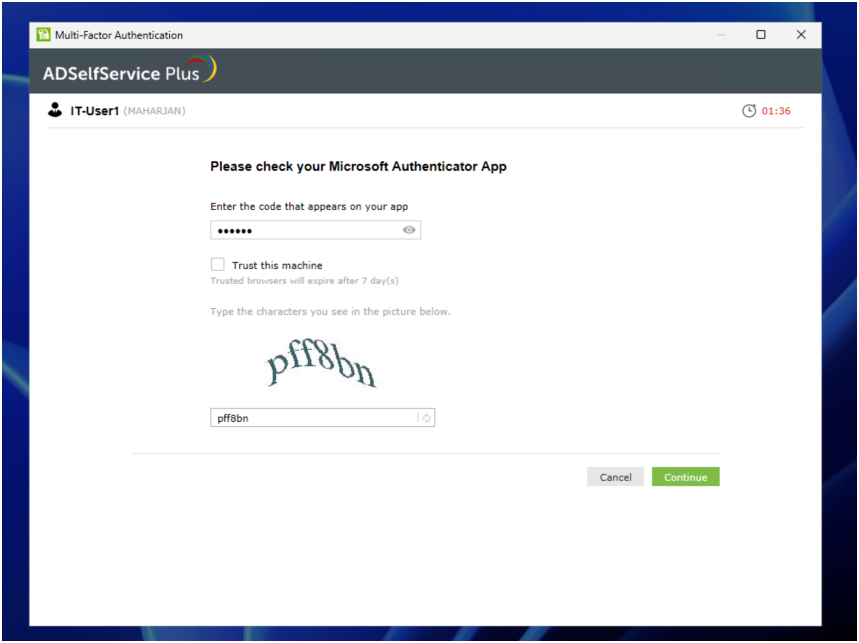
Done.
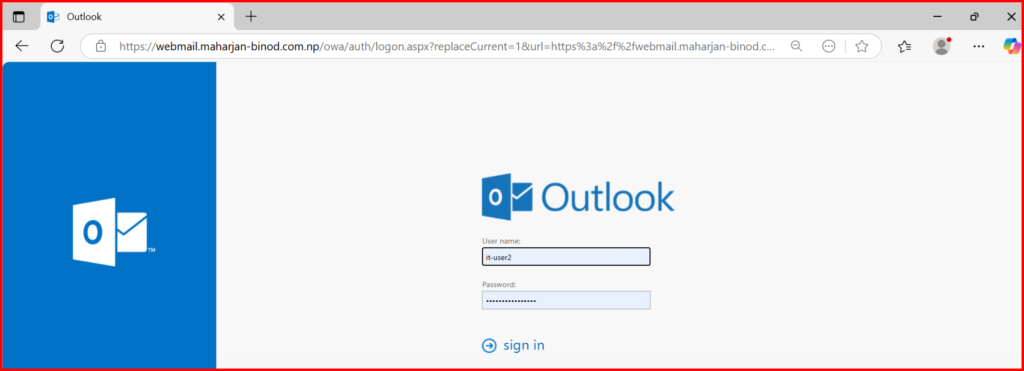
2. Test Exchange OWA MFA:
- Open browser and navigate to OWA.
- Login with test credentials.
- Confirm MFA challenge is required before access is granted.

3. Whatif, User need to Reset/Unlock/change Account&Password?
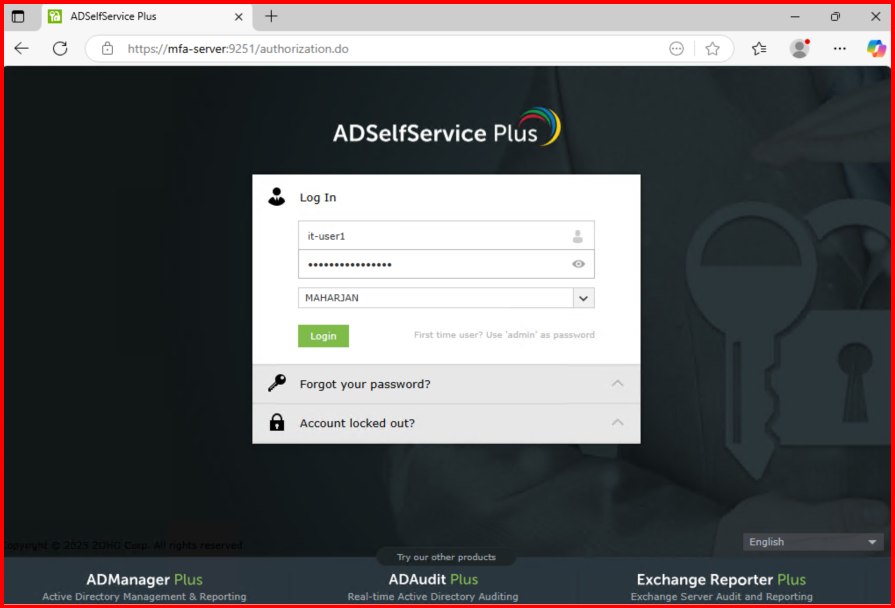
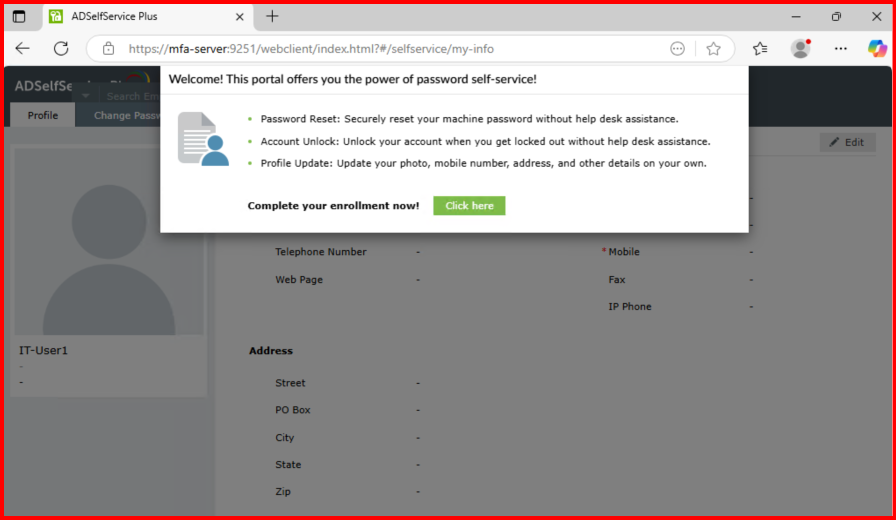
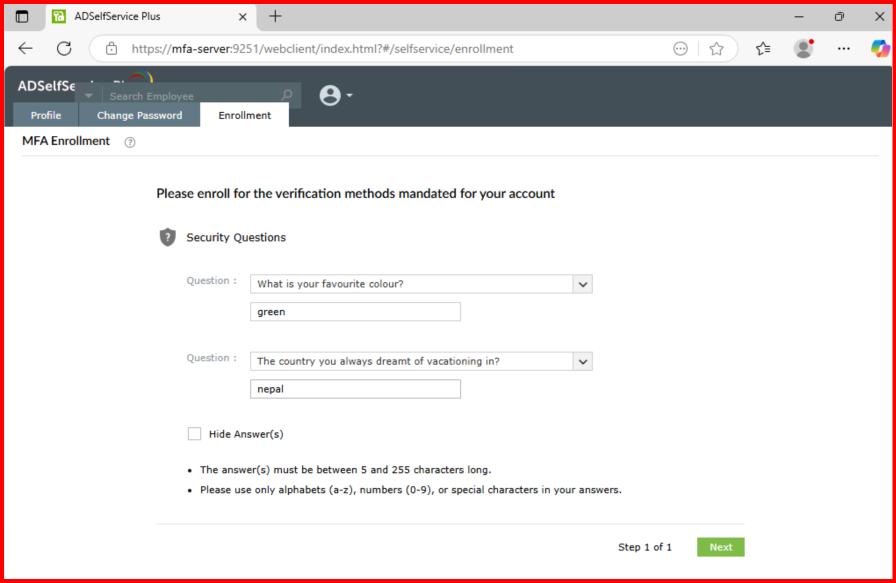
Setup MFA if there is alternative option enable:
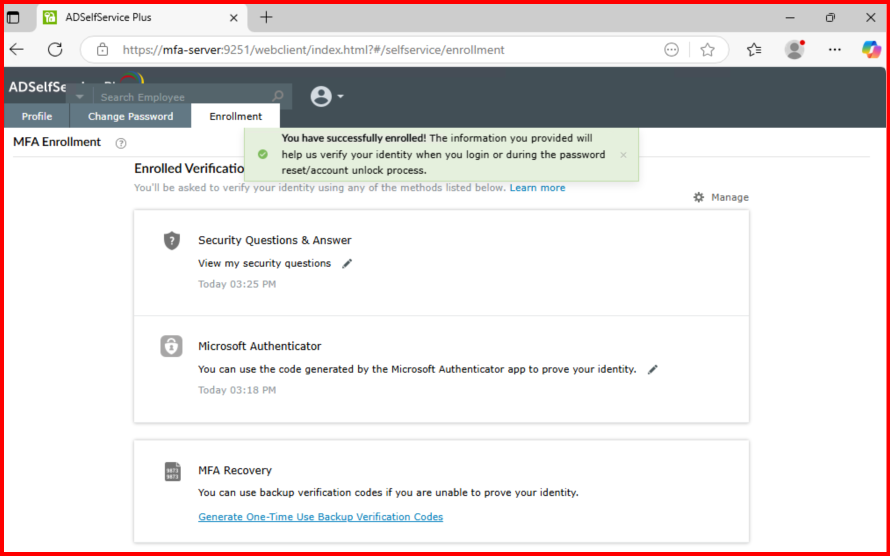
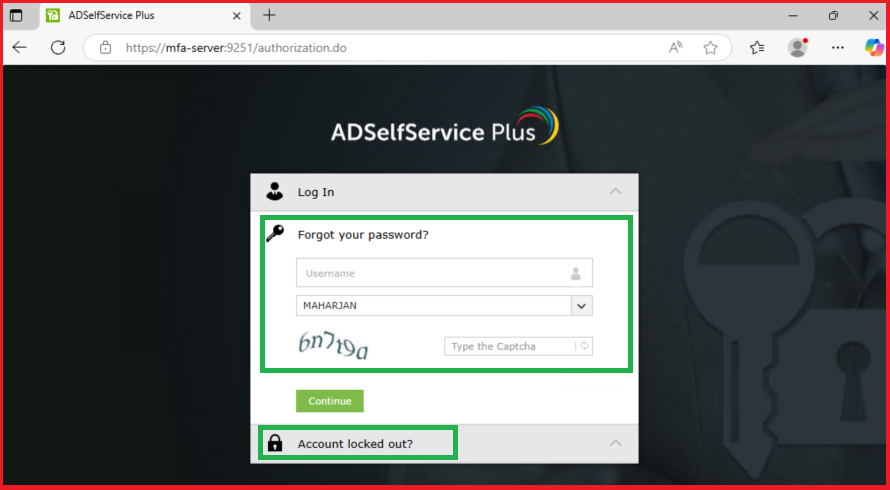
📝 Step 6: Troubleshooting Tips
- Ensure time is synchronized across all servers for Microsoft Authenticators.
- If OWA doesn’t prompt MFA:
- Check IIS logs.
- Ensure the connector is running.
- Validate policy assignment.
- For endpoint MFA issues:
- Confirm Logon Agent is properly installed.
- Review event logs under
Application and System.
Conclusion
Implementing MFA using ManageEngine ADSelfService Plus significantly enhances the security posture of both endpoint and email access. With just a few configurations, I was able to enforce MFA at critical access points — Windows login and Exchange OWA.
Leave a Reply