Introduction
In many Active Directory environments, any authenticated domain user can join up to 10 computers to the domain by default. While this might be convenient, it poses a security risk—unauthorized users can potentially add unmanaged devices, increasing your attack surface or complicating asset management. In this blog, I’ll show you how to restrict domain join permissions so only authorized users or groups can add computers to your domain.
Understanding Default Domain Join Permissions
Default Limit: The default limit is set to 10 machine accounts per user. This means that any authenticated user can join up to 10 machines to the domain without requiring additional permissions.
Exemptions: Users who are part of the Administrators or Domain Administrators groups, or those who have delegated permissions on containers in Active Directory to create and delete computer accounts, are not restricted by this limitation.
This default setting is often overlooked but can lead to potential security gaps.
✅ Goal
- Prevent all users from joining machines to the domain.
- Allow only a specific security group (e.g., Domain Joiners) to join computers.
- Secure all other OUs from unauthorized joins.
How to Restrict Domain Joining
There are several ways to restrict who can join computers to the domain but i prefer below option.
- Delegating Control: Delegate join permissions explicitly to a security group.
Step-by-Step Guide: Restrict Domain Join Permissions via ADUC
🔧 Step 1: Set MachineAccountQuota to 0
- Open Active Directory Users and Computers (ADUC) with an account that has permission to change security settings.
- Enable Advanced Features from the View menu to access security settings.
- Navigate to the domain name (maharjan.local)
- Right-click and select Properties > Security tab.
- Go to the Attribute Editor tab.
- Find and edit ms-DS-MachineAccountQuota, set it to 0.
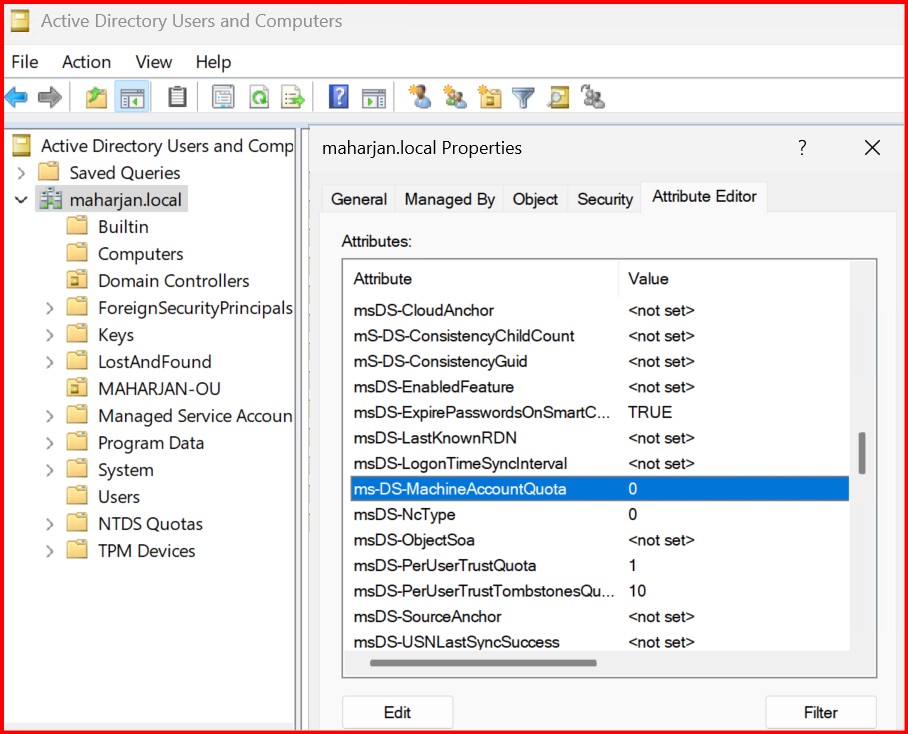
7. Click Apply and OK.
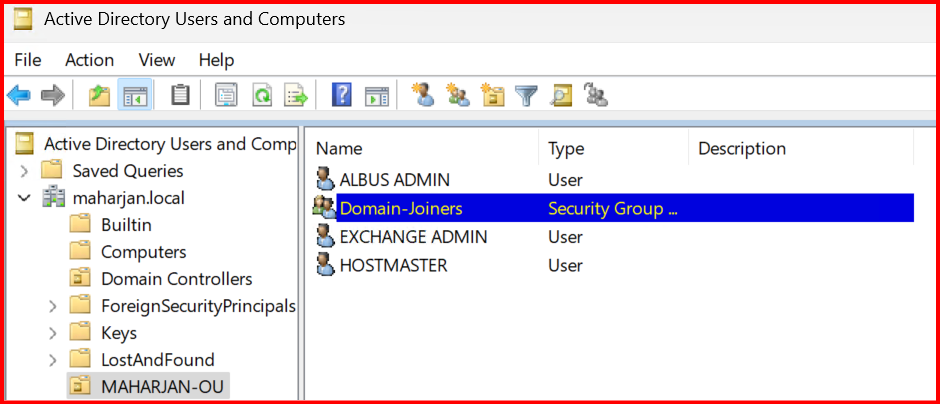
🔧 Step 2: Create a Security Group for Domain Joins
- Open ADUC.
- Create a new security group named Domain Joiners.
- Add users who should be allowed to join computers to this group.
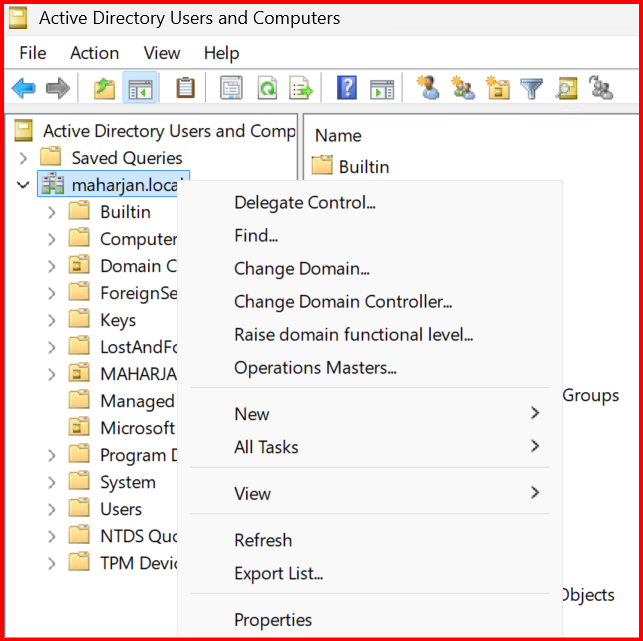
🔧 Step 3: Delegate Join Permissions
We need to give the Domain Joiners group permission to join the domain.
How to Delegate:
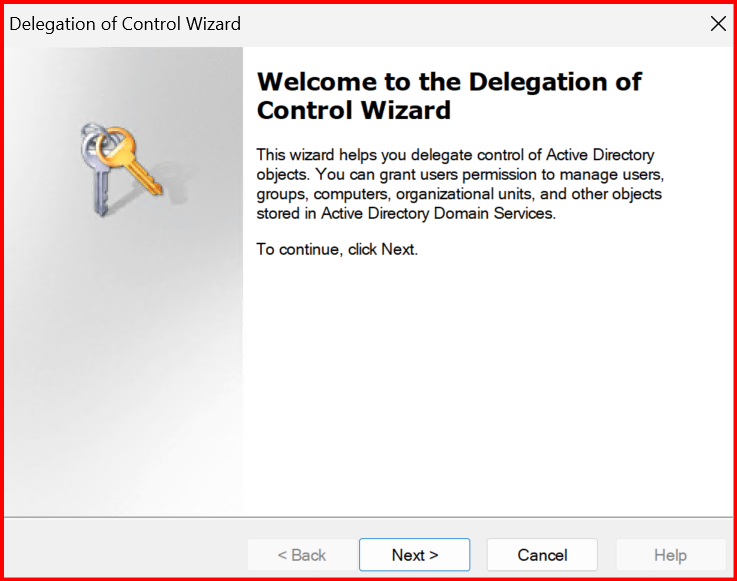
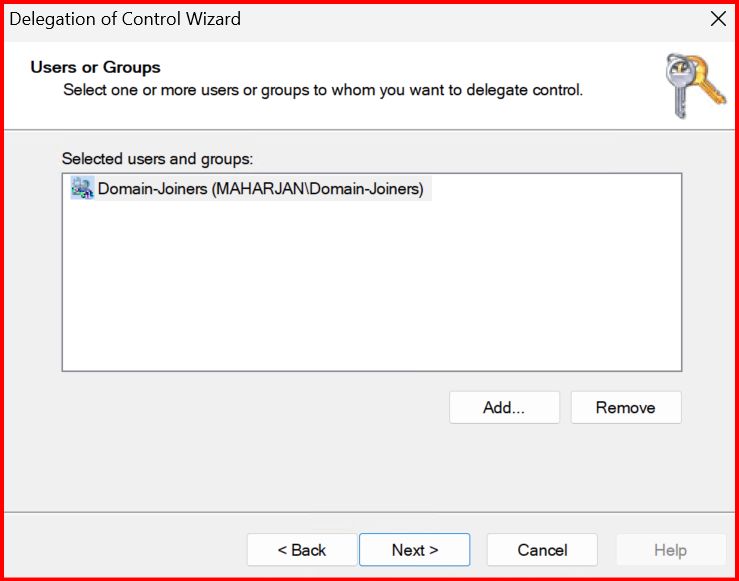
- Right-click the Domain (maharjan.local) > Delegate Control. Click Next.
- Add the Domain Joiners group. Click Next.
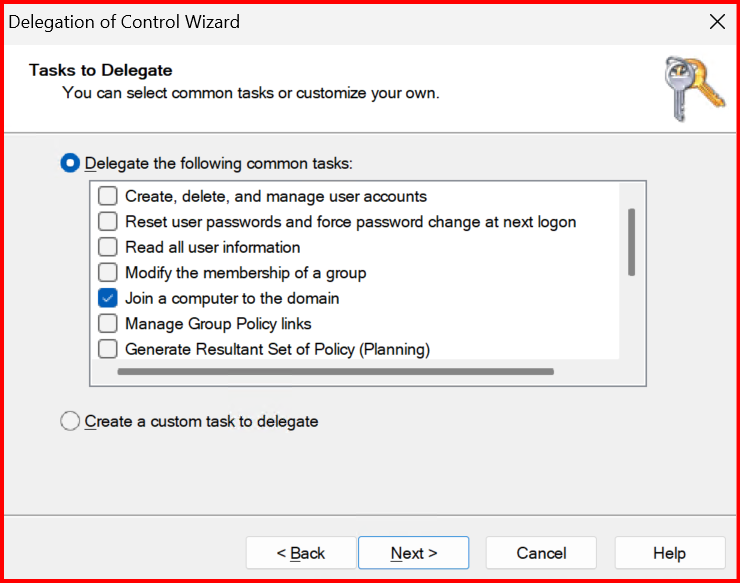
- Select the Join a computer to the domain. Click Next.
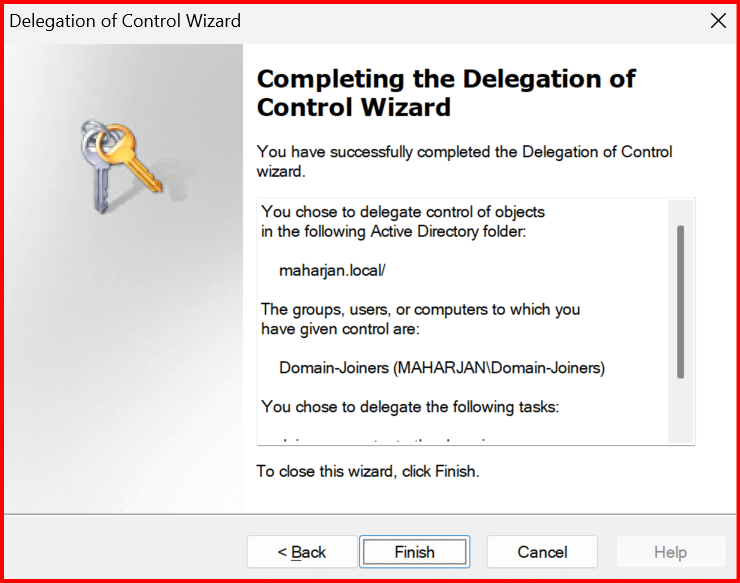
- Click Finish.
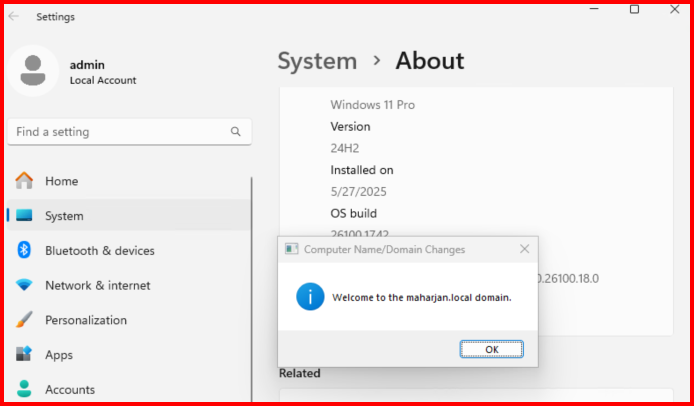
Testing the Changes
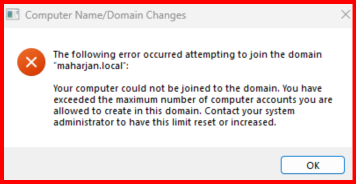
- Try to join a domain with a user who isn’t part of the allowed group. The join should fail with an access denied error.
- Confirm the authorized users can still join machines.
Best Practices
- Always delegate domain join permissions to a security group, not individual users.
- Regularly audit and review who has permission to join computers.
- Monitor event logs for failed domain join attempts (Event ID 4741 in Security logs).
- Document any changes made for compliance and auditing purposes.
🧠 Final Note
With this delegation:
- Users no longer consume quota (even if
ms-DS-MachineAccountQuotais set to 0). - They can only create/join computers in the OU they’ve been delegated for.
Conclusion
Restricting who can join computers to your domain is a simple yet powerful security step. By following the steps above, you ensure that only authorized users manage device additions, reducing security risks and improving control over your Active Directory environment.
Leave a Reply