Introduction
As a Windows Server admin, one of my top priorities is keeping systems secure—especially when it comes to local administrator accounts. That’s where LAPS (Local Administrator Password Solution) comes in.
With Windows Server 2025, Microsoft has integrated the new LAPS features natively into the OS, making it even easier to manage local admin passwords securely without needing a separate installation.
🧠 What Is LAPS and Why Do We Need It?
Every system in the domain has a local admin account. If all these machines use the same password for this account, it becomes a huge security risk—anyone who knows the password can access every machine!
LAPS solves this by:
- Automatically setting a unique, random password for the local admin account on each machine.
- Storing these passwords securely in Active Directory.
- Ensuring only authorized users can retrieve the passwords.
🆕 What’s New in Windows Server 2025 LAPS?
With Windows Server 2025, LAPS is built-in, and here are some new features:
- ✅ Event logging for password retrieval.
- ✅ Automatic rotation of passwords on-demand.
- ✅ Enhanced group policy settings.
- ✅ Support for both legacy and new LAPS simultaneously (for migration).
🛠️ Step-by-Step: How I Configured LAPS in Windows Server 2025
1️⃣ Enable the LAPS Feature
LAPS is already included in Windows server 2025 OS.
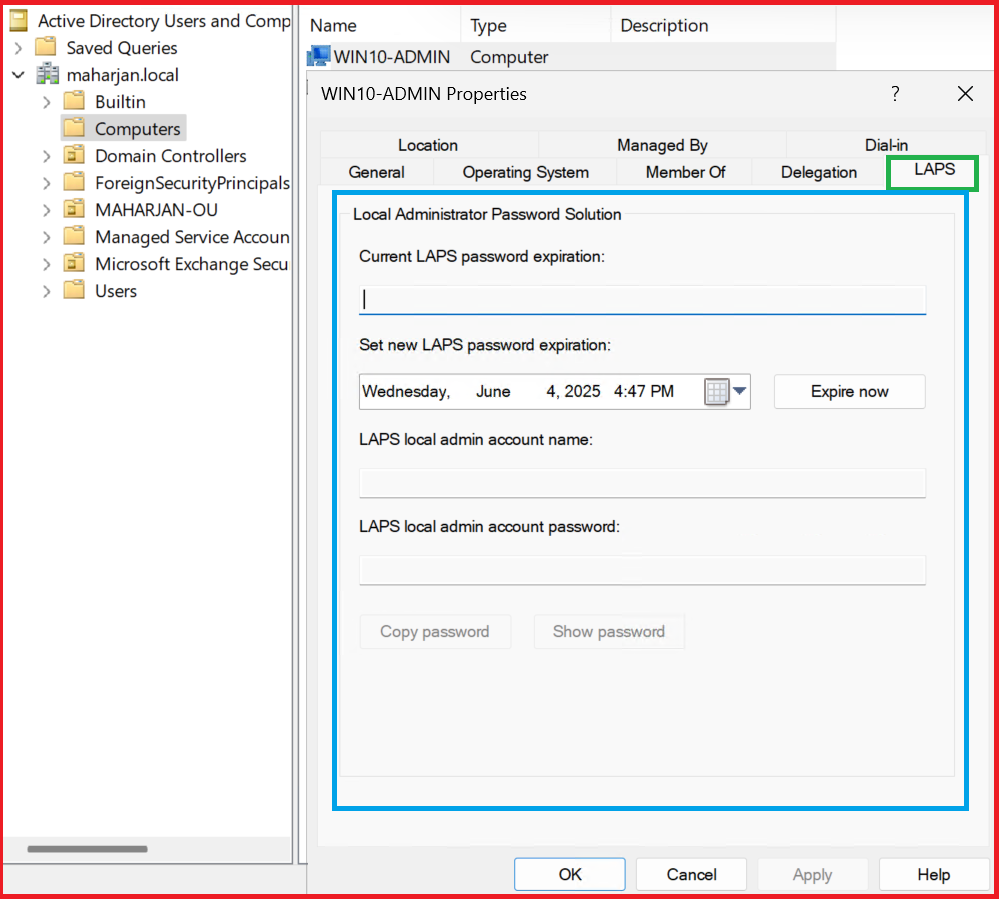
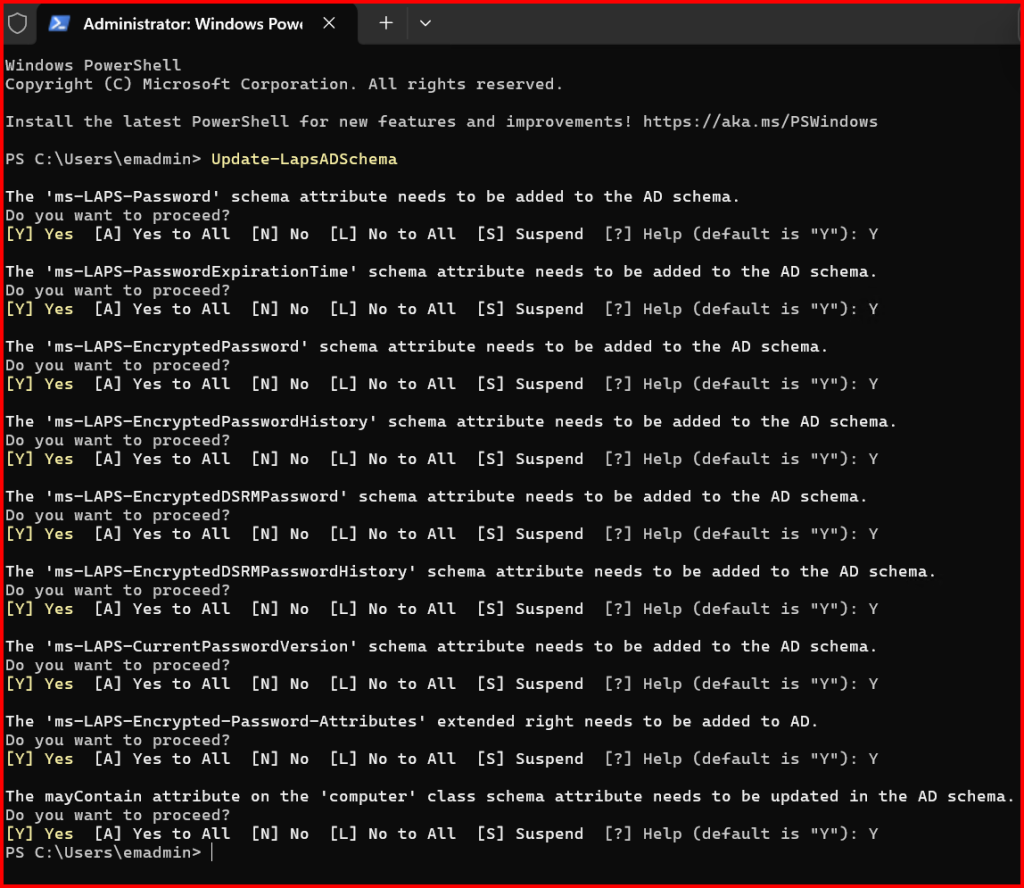
2️⃣ Extend the AD Schema (Only Once)
I ran this on my schema master:
Update-LapsADSchema
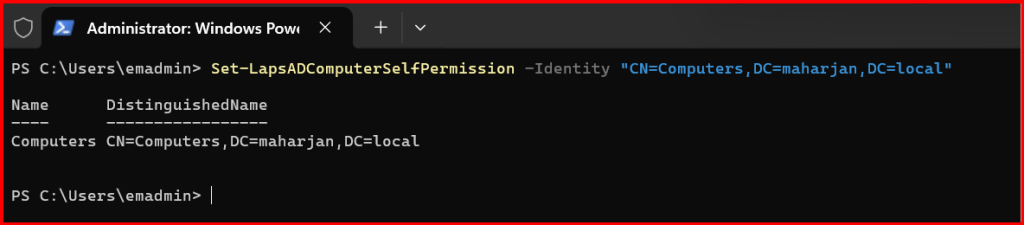
3️⃣ Set Permissions for Computers to Write Their Passwords
Each computer must be able to write its password to its AD object. I used:
Set-LapsADComputerSelfPermission -Identity "CN=Computers,DC=maharjan,DC=local"
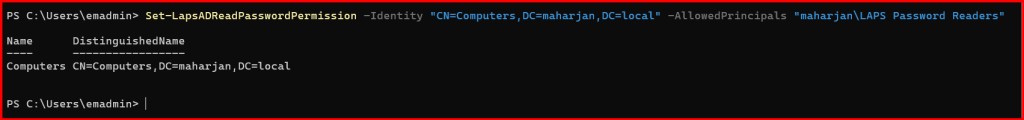
4️⃣ Grant Read Access to Helpdesk/Admin Team
Only specific groups should be allowed to read LAPS passwords:
Set-LapsADReadPasswordPermission -Identity "CN=Computers,DC=maharjan,DC=local" -AllowedPrincipals "maharjan\LAPS Password Readers"
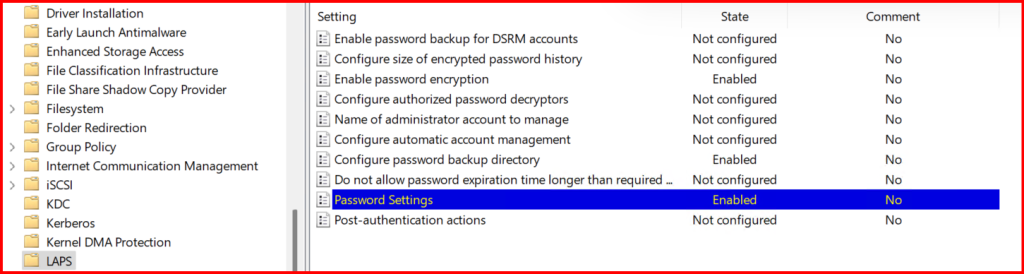
5️⃣ Configure Group Policy
I opened Group Policy Management and set:
Computer Configuration > Administrative Templates > System > LAPS
- Enable LAPS: Enabled
- Name of administrator account: (leave blank for default Administrator)
- Password settings: complex, 30 days rotation
- Configure Password Backup directory: Active Directory
6️⃣ Verify It’s Working
On a client machine, I ran:
Get-LapsDiagnostics

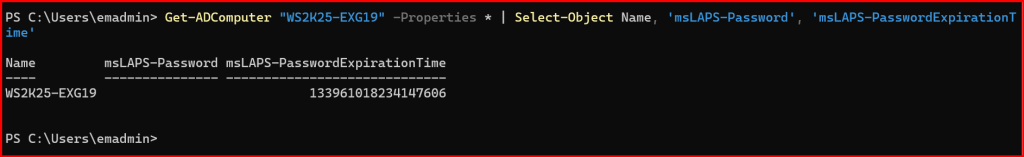
And I checked the AD computer object’s attributes using:
Get-ADComputer "WS2K25-EXG19" -Properties * | Select-Object Name, 'msLAPS-Password', 'msLAPS-PasswordExpirationTime'
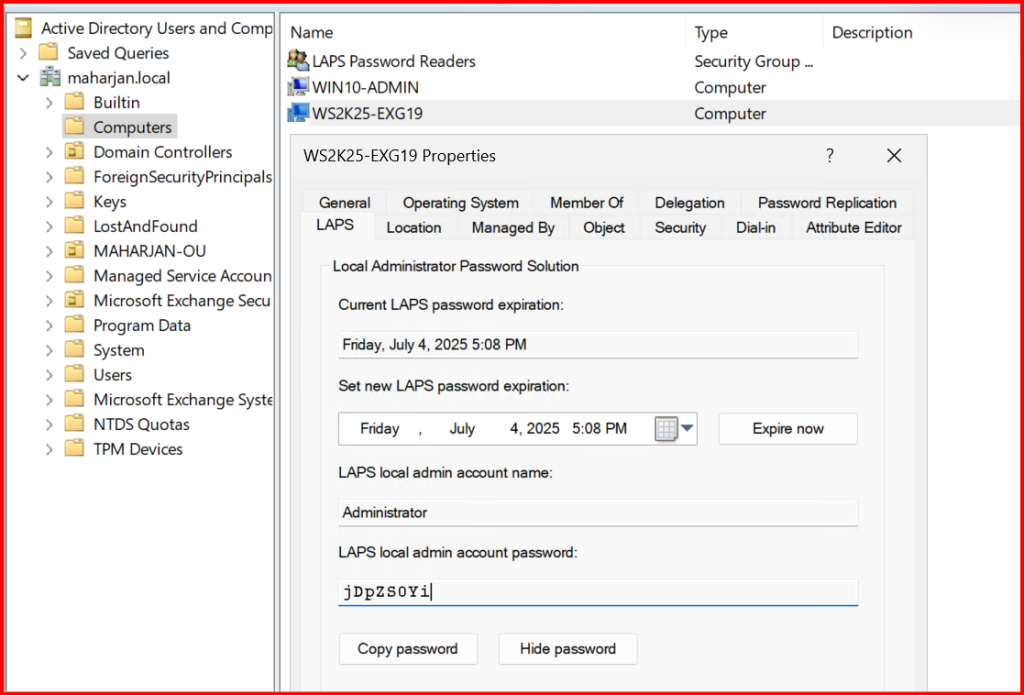
🔍 Viewing Passwords Securely
To view a password:
Get-LapsADPassword -Identity "WS2K25-EXG19"
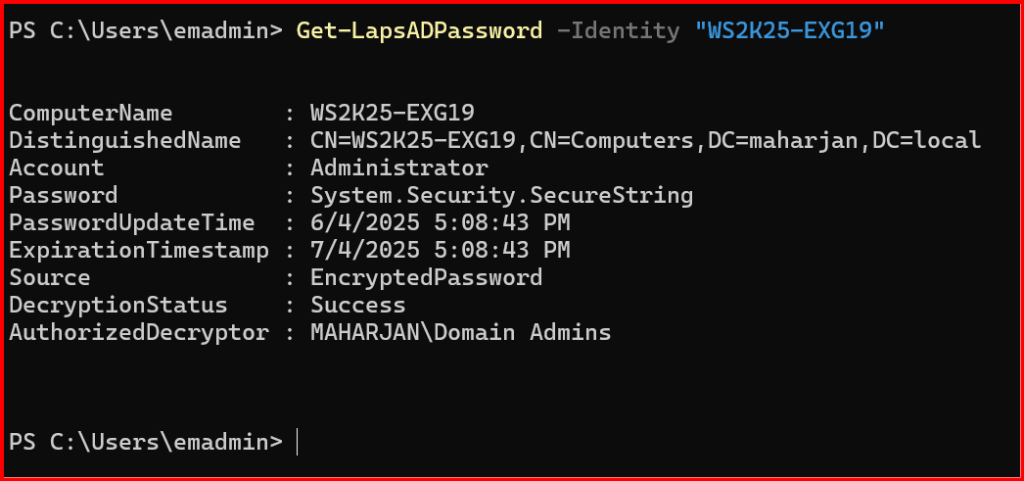
Issue Resolved to view password:
Get-LapsADPassword -Identity “WS2K25-EXG19” -AsPlainText
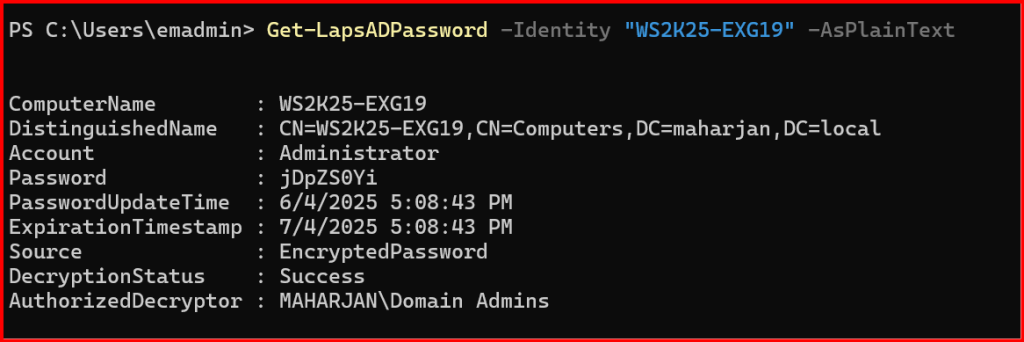
Only authorized admins can do this.
🛡️ Security Best Practices I Follow
- 🔒 Use a dedicated AD group for LAPS password readers.
- 🧾 Monitor LAPS password retrieval logs (Event ID 10038).
- 🔁 Set shorter password expiration (e.g., every 30 days).
🧭 Final Thoughts
With Windows Server 2025, managing local admin passwords is more secure and seamless than ever. No more shared passwords, no more manual resets, and peace of mind that each system is protected.
Have you tried the new LAPS yet? Let me know your thoughts or issues in the comments!
Leave a Reply