As part of my ongoing efforts to secure my Exchange Server, I decided to restrict access to the Exchange Control Panel (ECP) to only a few trusted IP addresses. This helps minimize the attack surface, especially since ECP is a web-based interface that could be a potential target for brute-force or credential stuffing attacks.
📌 Why I Did This
ECP is usually accessible via https://mail.domain.com/ecp. By default, it’s open to anyone who has credentials, even from the public internet. While strong passwords and MFA are essential, restricting access to only my admin workstation IPs gives me an additional layer of security.
🔧 Steps I Followed to Restrict ECP Access by IP Address
I’m running Exchange Server 2019 on Windows Server 2025, and here’s how I set up the IP restrictions:
1. Open IIS Manager
- On the Exchange server, I opened Internet Information Services (IIS) Manager.
- I navigated to:
Default Web Site > ecp
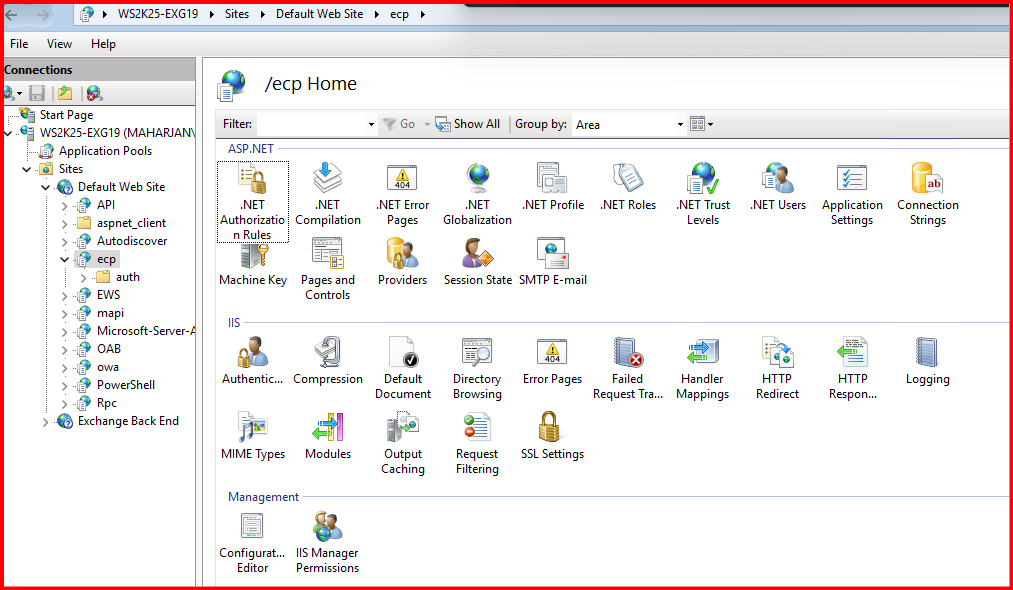
In my case, I have not installed the features, “IP Address and Domain Restrictions” yet so not shown.
2. Enable IP and Domain Restrictions
- If IP and Domain Restrictions wasn’t already installed, I did:
- Open Server Manager > Add Roles and Features > Web Server (IIS) > Web Server > Security, and selected IP and Domain Restrictions.
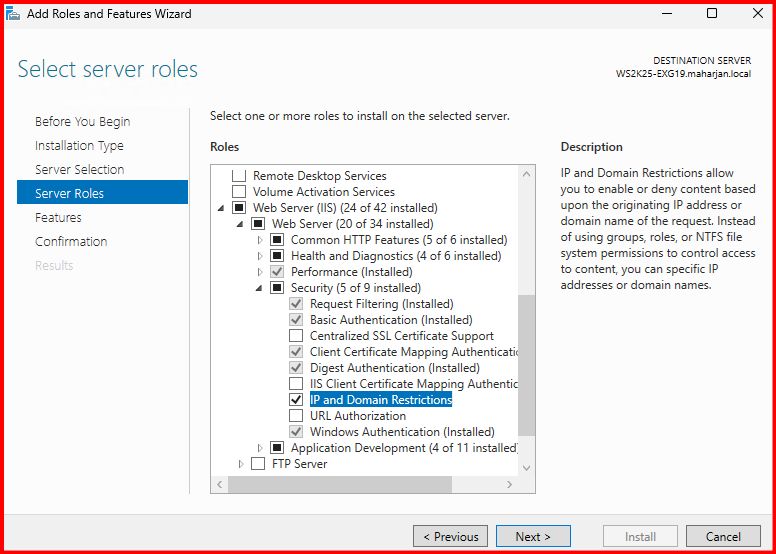
- Then in IIS Manager under the ecp site, I opened IP Address and Domain Restrictions.
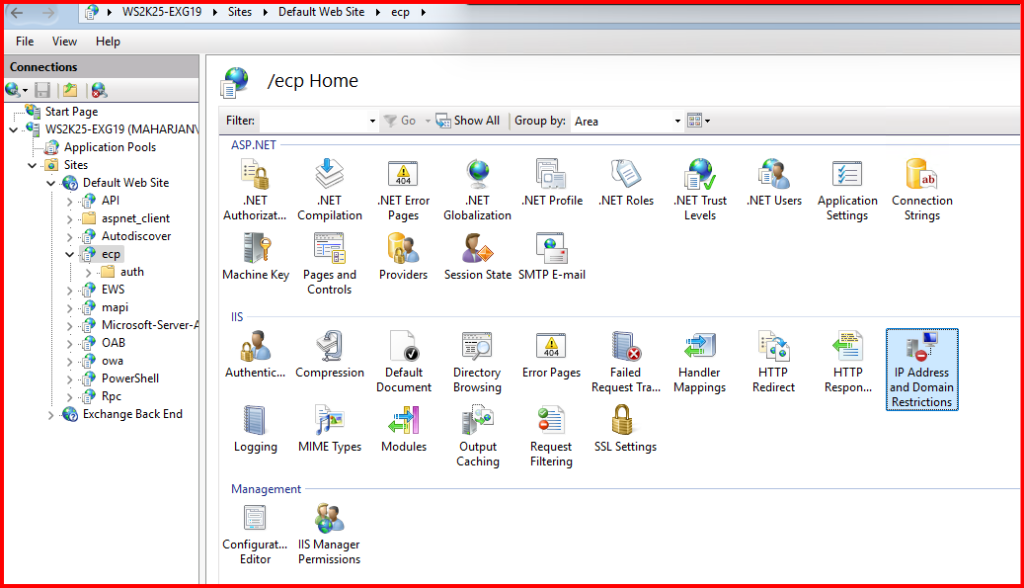
3. Configure IP Restrictions
- I clicked on “Add Allow Entry…” and added the specific IPs or IP ranges I wanted to allow (e.g., Only Exchange Server IP).
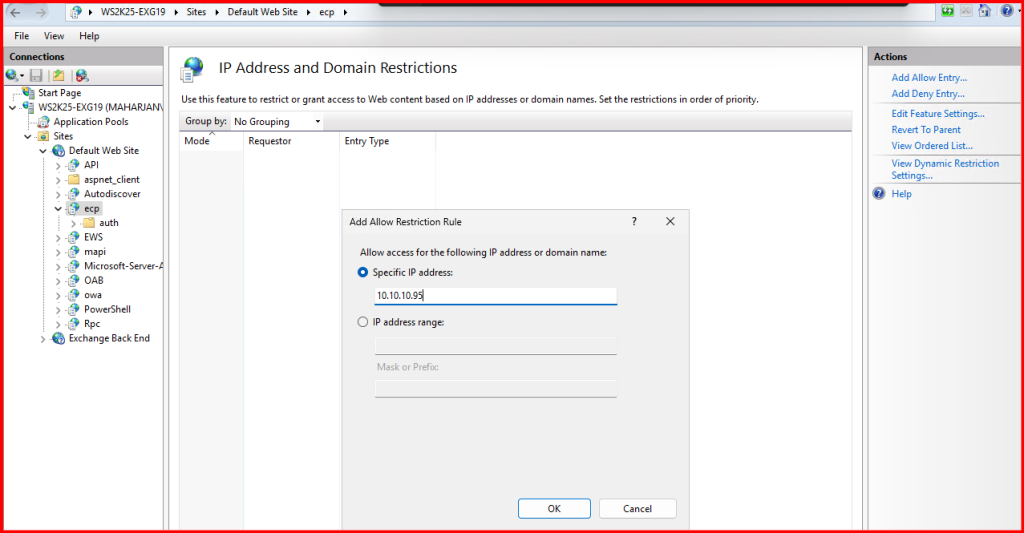
- Then I clicked “Edit Feature Settings…” on the right pane and selected:
- Deny for unspecified clients
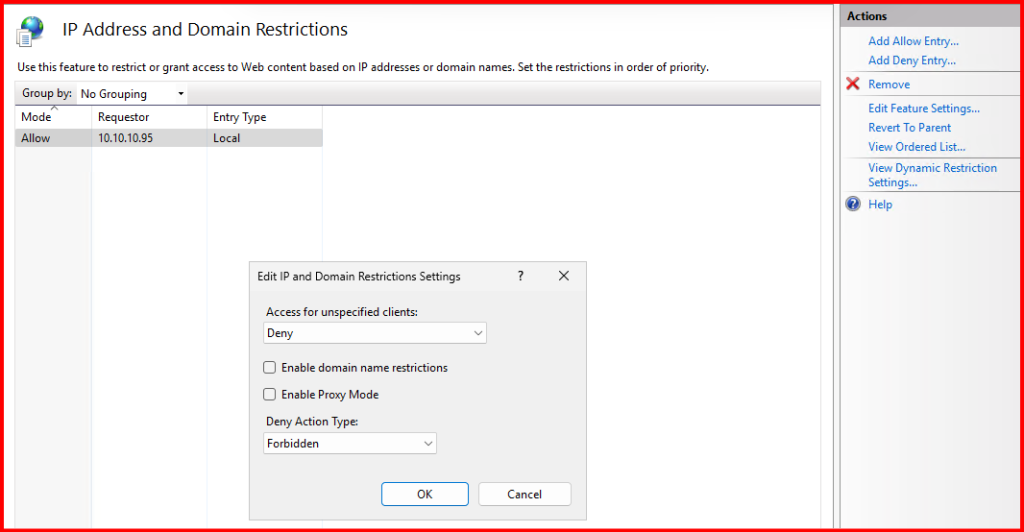
This way, only allowed IPs can access the ECP, and all others are denied.
Alternatively, I clicked on “Add Deny Entry…” and added the specific IP to deny ECP.
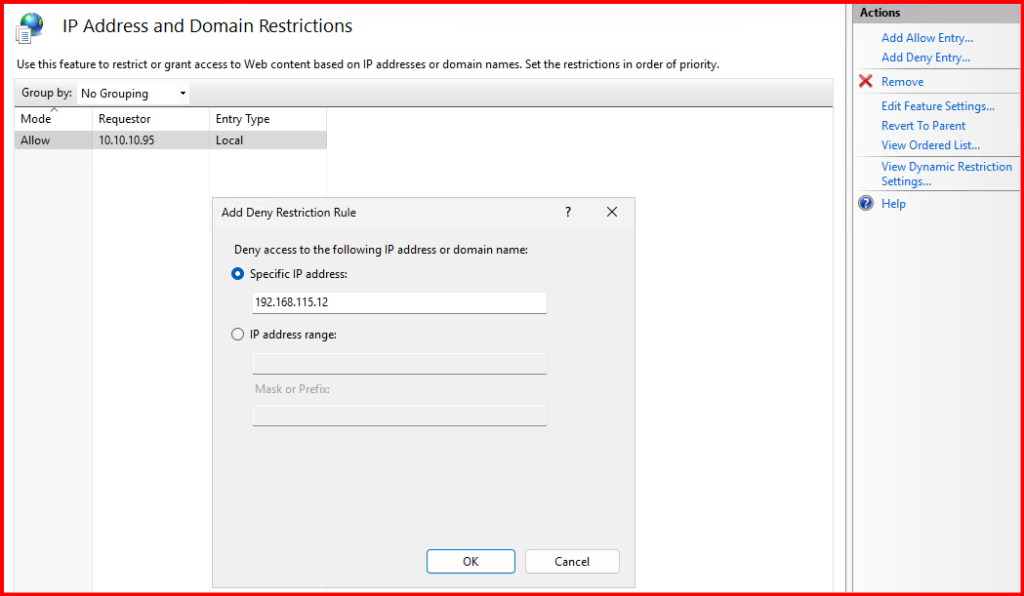
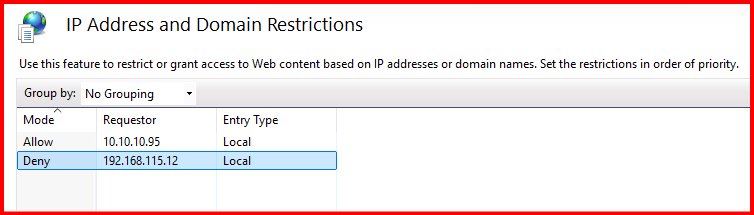
⚠️ Important Notes
- These changes do not affect OWA access, so users can still access email via
/owa. - If you’re using a load balancer or reverse proxy, make sure the real client IP is being forwarded correctly.
- Always test the changes from an allowed IP to avoid locking yourself out!
🧪 How I Verified It Worked
From a browser outside the allowed IP range, trying to access /ecp. From my allowed admin IP, everything worked fine but from restricted IP, it denied.
Option1: Tested with Deny action type: Forbidden, Unauthorized and Not Found options.
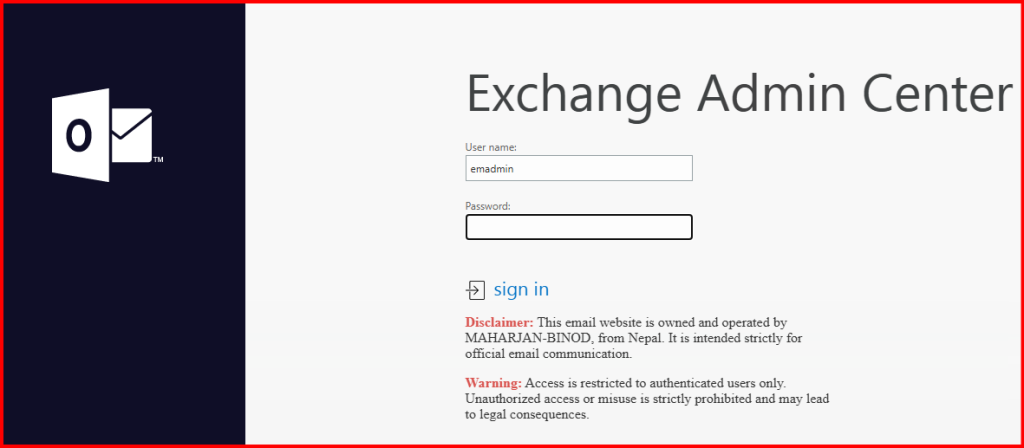
Result: After typing password and sign in clicked, I got no respond and warning message. Hence, ECP login is denied.
Option2: Tested with Deny action type: Abort
Result: I got respond with:
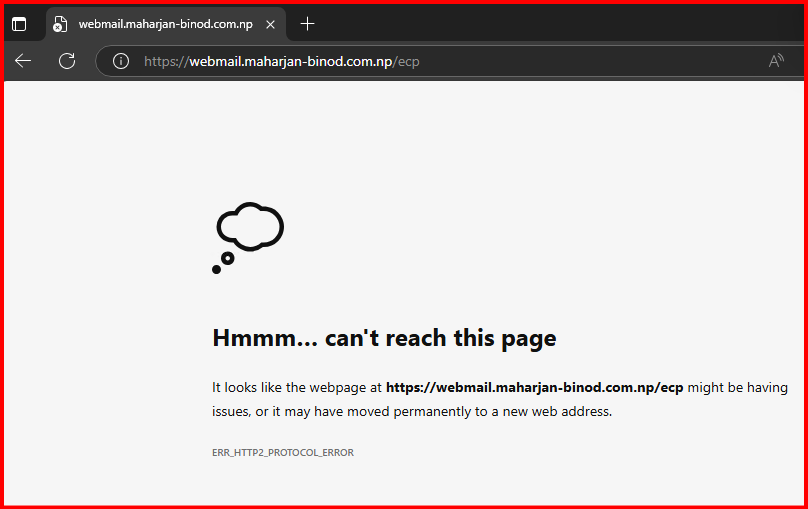
✅ Extra Hardening Tips
- Use MFA for all admin accounts.
- Consider separating ECP to a different virtual directory or disabling it entirely for non-admin accounts.
- Monitor IIS logs regularly for suspicious access attempts.
📝 Conclusion
Restricting ECP login by IP is a quick win in hardening your Exchange Server. It’s especially useful if you’re managing your environment remotely or hosting Exchange in a public-facing setup.
Leave a Reply