When managing Exchange Server, the Exchange Management Shell (EMS) is one of the most powerful tools at my disposal. But with great power comes great responsibility—especially when it comes to security. In this post, I’ll walk through best practices for securing EMS to prevent unauthorized access and reduce risk in an enterprise environment.
What is Exchange Management Shell?
EMS is a PowerShell-based command-line interface that provides administrators with full access to Exchange Server configuration. It builds on Windows PowerShell and includes Exchange-specific cmdlets for tasks like mailbox management, transport configuration, and server diagnostics.
While EMS is incredibly efficient for automation and scripting, it can also become a security liability if not properly locked down.
Why Securing EMS is Critical
Here’s why I take EMS security seriously:
- Privilege escalation: Unauthorized access to EMS gives full control over the Exchange organization.
- Remote access vectors: EMS can be opened via remote PowerShell, increasing attack surfaces.
- Script misuse: Malicious scripts can be executed if the shell is not properly monitored or controlled.
Key Ways I Secure Exchange Management Shell
1. Restrict EMS Access with Role-Based Access Control (RBAC)
RBAC lets me define who can run what in EMS. Instead of granting full Exchange Admin access, I create custom management roles with limited cmdlets and assign them to specific users or groups.
New-ManagementRole -Name "Helpdesk Mailbox Management" -Parent "Mail Recipients"
New-RoleGroup -Name "Helpdesk Team" -Roles "Helpdesk Mailbox Management" -Members IT-user1, IT-user2

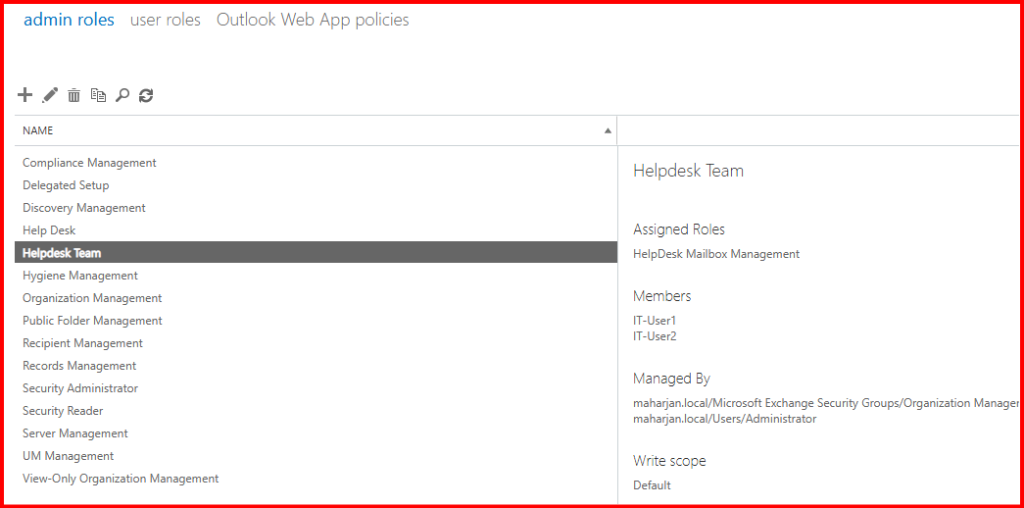
Let’s open EMS using the IT-user2 account and see what actions I can perform.
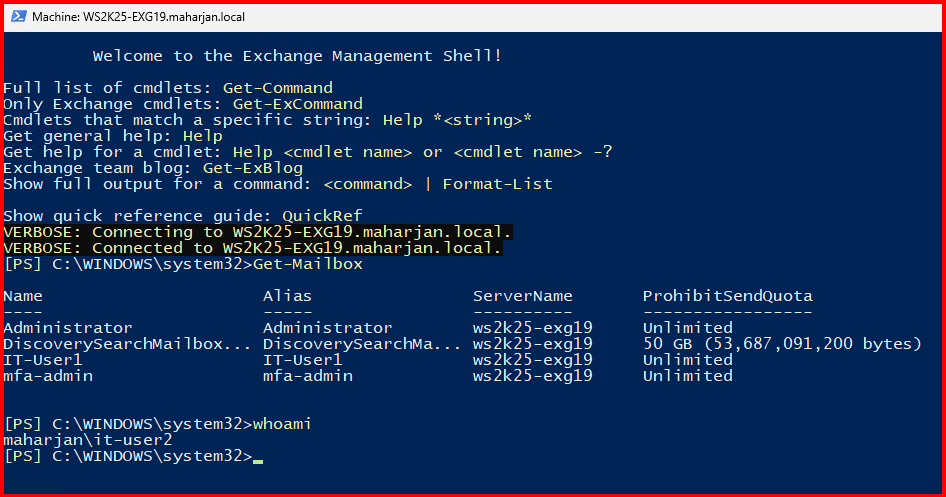
Note: I can run Get- and Set- commands, but not New- commands.
I also rechecked by logging in through ECP. I cannot create a new mailbox, but I can modify existing ones and have limited privileges.
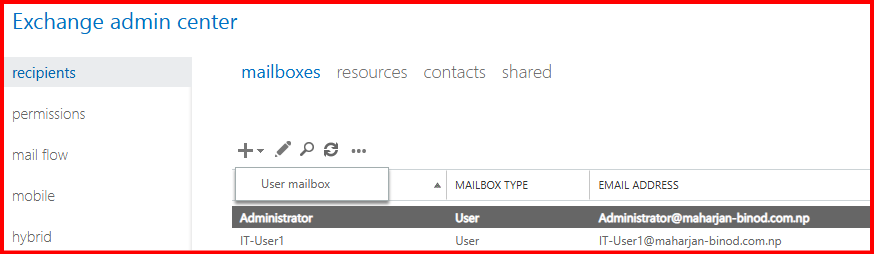
2. Enable Just Enough Administration (JEA)
I use JEA with PowerShell constrained endpoints to allow specific administrative tasks without giving full admin privileges. This limits exposure and reduces the risk of human error or compromise.
To be honest, by default, a client PC joined to the domain network can connect easily using Kerberos, without any password prompts. However, when JEA is configured, users will have limited permissions.
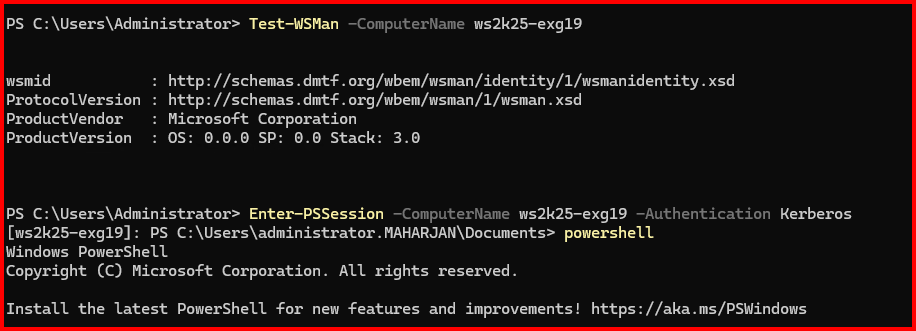
3. Disable Remote PowerShell Where Not Needed
Remote Exchange Management Shell (EMS) is a common attack vector. I ensure that only authorized users have access by disabling it for others.
1. List All Users with Remote PowerShell Enabled
This helps with periodic audits:
Get-User -ResultSize Unlimited | Where-Object { $_.RemotePowerShellEnabled -eq $true } | Select Name, UserPrincipalName
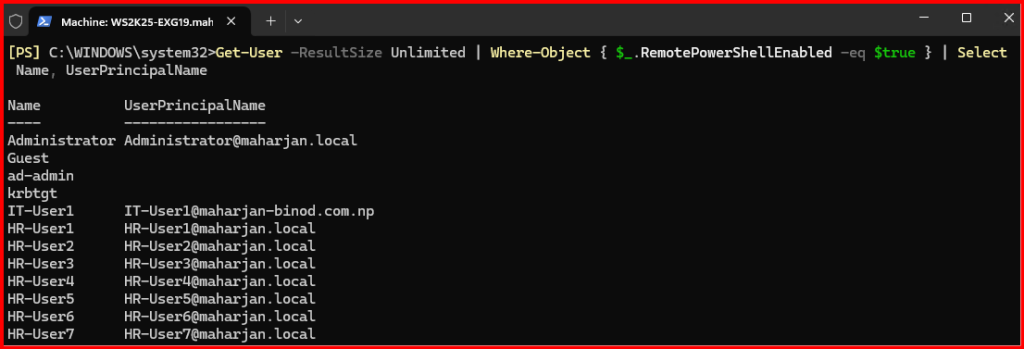
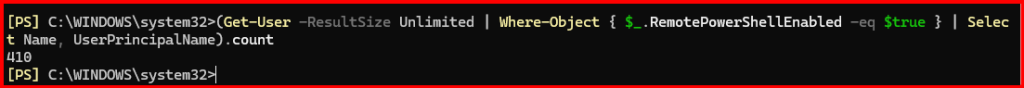
2. Disable all Remote PowerShell Enable Users
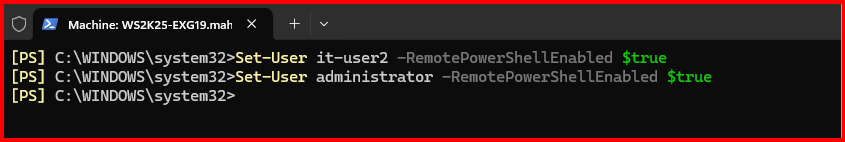
3. Enable Remote PowerShell For specific Users
Use the following command in Exchange Management Shell to disable remote PowerShell access:
Set-User administrator -RemotePowerShellEnabled $true
Set-User it-user2 -RemotePowerShellEnabled $true
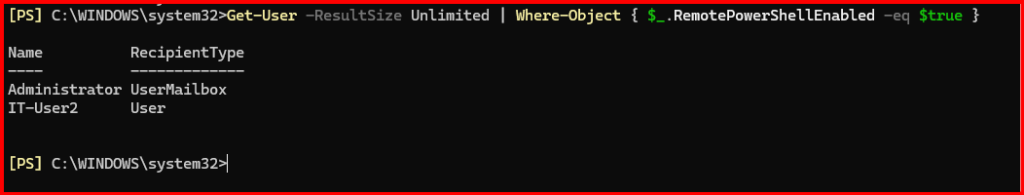
I also monitor the list of users with remote PowerShell enabled and regularly audit them and export reports.
Get-User -ResultSize Unlimited | Where-Object { $_.RemotePowerShellEnabled -eq $true } | Export-Csv "C:\Audit\RemotePowerShellUsers.csv" -NoTypeInformation
4. Use Secure Protocols and Authentication
I ensure that Exchange Management Shell (EMS) sessions are accessed securely — over HTTPS (port 443), with Kerberos or certificate-based authentication.
I strictly avoid using Basic Authentication over HTTP, as it’s insecure and exposes credentials in cleartext.
Confirm HTTPS Listener Is Enabled on Exchange Server
Check if WinRM has an HTTP/HTTPS listener:
winrm enumerate winrm/config/listener
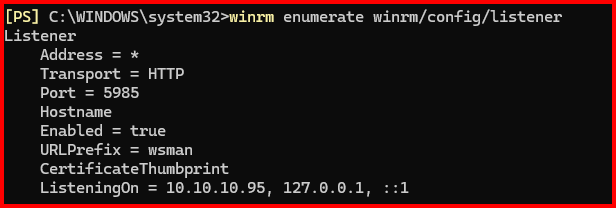
If Missing: Create a WinRM HTTPS Listener.
Note: Refer to the official documentation.
5. Audit and Monitor EMS Activity
Logging is my best friend here. I enable PowerShell transcription logging, Exchange Admin Audit Logging, and integrate with SIEM solutions to track all EMS activity. These logs help me trace commands, detect anomalies, and maintain compliance.
1. Enable Exchange Admin Audit Logging (EAAL)
This logs all cmdlets run by admins through EMS, ECP, or Remote PowerShell.
Set-AdminAuditLogConfig -AdminAuditLogEnabled $true

2. Review and Filter Audit Logs
To search recent actions:
Search-AdminAuditLog -StartDate (Get-Date).AddDays(-7) -EndDate (Get-Date)
To filter specific cmdlets:
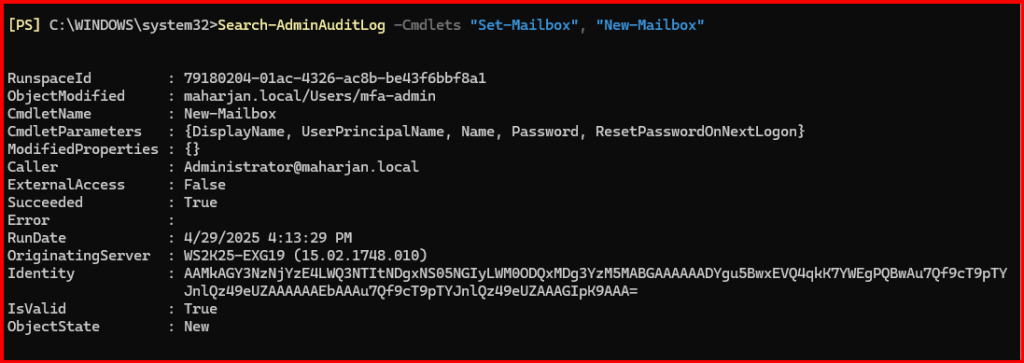
Search-AdminAuditLog -Cmdlets "Set-Mailbox", "New-Mailbox"
Export to CSV for offline review:
Search-AdminAuditLog | Export-Csv C:\Audit\AdminAuditLog.csv -NoTypeInformation
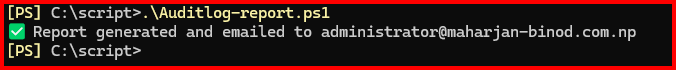
You can download full scripts to see in html report and in email.
6. Limit Script Execution Policy
To prevent malicious or unapproved scripts from running in EMS, I set a strict execution policy.
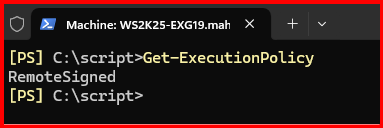
Set-ExecutionPolicy RemoteSigned
Note: If not, set it to RemoteSigned.
This blocks unsigned or downloaded scripts from executing without manual review.
7. Keep Exchange and OS Updated
Security patches often include fixes for EMS-related vulnerabilities. I stay on top of patch cycles for both Exchange Server and Windows Server.
Final Thoughts
The Exchange Management Shell is a powerful administrative interface, but without proper security controls, it can become a backdoor for attackers. By implementing RBAC, disabling unnecessary remote access, enforcing secure authentication, and actively auditing usage, I make sure EMS remains a tool—not a threat.
If you haven’t reviewed your EMS security posture recently, now is a good time to start!

Leave a Reply